Splunk SOAR Cloud & on-premise monitoring and active actions in TrackMe
Hint
Version 2.0.46 and later
The SOAR integration requires TrackMe version 2.0.46 and later
SOAR High Availability management for Automation Brokers is available from TrackMe version 2.0.50 and later
Hint
New since TrackMe 2.1.10: REST lookup capabilities and review of the adhoc/playbook failure detections use cases
In TrackMe 2.1.10, we have introduced a new REST lookup capability with the command
trackmesplksoarlookupand fully refactored the adhoc and playbook failure detections use cases to leverage this new capability.With this command, TrackMe performs REST based live lookups to SOAR, allowing to retrieve the metadata associated with the SOAR objects such as the playbooks, assets, applications and brokers associated with the detection.
These metadata information are then added to the extra_attributes field of the resulting entities, allowing to have a full context of the detection and to be able to review the details of the detection directly from the TrackMe UI.
Hint
New since TrackMe 2.1.11: REST based SOAR monitoring of playbooks run concurrency and statuses
In TrackMe 2.1.11, we have introduced a new REST based SOAR monitoring of playbooks run concurrency and statuses, leveraging the REST lookup capabilities.
This allows to monitor the concurrency of playbooks run and their statuses, and to be alerted in case of issues.
This is available out of the box with the use case
splk_soar_concurrent_playbooks.
Splunk Remote Account: You must use the trackme namespace
If you use a remote account to run the SOAR active monitoring (Automation Brokers High Availability), you must use the TrackMe namespace when configuring the Splunk remote account.
This is required because TrackMe by default is shared at the application level, so unless you share TrackMe at the system level, your remote account would not be able to access to TrackMe custom commands on the remote partner.
1. Introduction to SOAR monitoring
TrackMe provides builtin use cases to actively and efficiently monitor at scale one or more Splunk SOAR environments.
SOAR Cloud & on-premise monitoring is performed via the TrackMe Flex Object component (splk-flx) which is a restricted component not available with the Free community edition of TrackMe.
The monitoring relies on TrackMe’s SOAR integration and the Splunk Application for SOAR integration, associated with TrackMe’s Flex Object concepts, and provides the following use cases:
uc_ref |
uc_description |
uc_implementation_comments |
|---|---|---|
|
Monitor the concurrency of playbooks run |
This use case relies on SOAR events indexed in Splunk through the Splunk Application for SOAR integration. It monitors for playbooks run concurrency and triggers an alert if the concurrency limit is exceeded. This use case also leverages a live REST API lookup capability to retrieve the SOAR object context metadata. |
|
Monitor for SOAR adhoc actions failures |
This use case relies on SOAR events indexed in Splunk through the Splunk Application for SOAR integration. It monitors for app run action failures and triggers shall there be any failures, the alert will clear itself once failures cannot be found in the time range. You may want to adapt the search time range according to your preferences to keep the alert active for a certain amount of time after detection happened. This use case also leverages a live REST API lookup capability to retrieve the SOAR object context metadata. |
|
Monitor for SOAR playbook actions failures |
This use case relies on SOAR events indexed in Splunk through the Splunk Application for SOAR integration. It monitors for playbook action failures and triggers shall there be any failures, the alert will clear itself once failures cannot be found in the time range. You may want to adapt the search time range according to your preferences to keep the alert active for a certain amount of time after detection happened. This use case also leverages a live REST API lookup capability to retrieve the SOAR object context metadata. |
|
Runs an active assets health check, parse and render results |
This use case relies on TrackMe’s SOAR integration and the Splunk App for SOAR integration, if active_check is set to True, it performs an active asset health check (connectivity test) by discovering assets, running a POST call to request the connectivity test, then parses and renders results for each asset. If active_check is set to False, it simply parses assets and checks the latest connectivity test achieved by SOAR and renders results. Running the active check requires the automation user in SOAR to have the edit asset permissions, if you do not want this or cannot set it, you can disable the active check and rely on SOAR doing it automatically once per day, therefore a failure detection can take up to 24 hours, enable active check is recommended. The soar_server can be specified with the option soar_server=<account>, if unspecified or set to *, the first account will be used. You can restrict the list of assets to be taken into account using the assets_allow_list option, and/or avoid some assets to be taken into account using assets_block_list option. The SOAR automation used for the SOAR server account configuration needs to be able to update assets if active check is enabled as it performs an active test request against the SOAR REST API. |
|
Monitor SOAR CPU load from the SOAR API health endpoint |
This use case relies on TrackMe’s SOAR integration and the Splunk App for SOAR integration, it retrieves the 1/5/15 minutes CPU load performing a GET call to the health endpoint. The soar_server can be specified with the option soar_server=<account>, if unspecified or set to *, the first account will be used. |
|
Monitor SOAR CPU load from the SOAR API health endpoint |
This use case relies on TrackMe’s SOAR integration and the Splunk App for SOAR integration, it retrieves and calculates the percentage of memory usage of the SOAR instance performing a GET call to the health endpoint. The soar_server can be specified with the option soar_server=<account>, if unspecified or set to *, the first account will be used. |
|
Get the status of SOAR services from the SOAR API health endpoint |
This use case relies on TrackMe’s SOAR integration and the Splunk App for SOAR integration, retrieving the status of SOAR services performing a GET call to the health endpoint. The soar_server can be specified with the option soar_server=<account>, if unspecified or set to *, the first account will be used. |
|
Monitor the status of SOAR Automation Brokers and optionally update SOAR Assets for High Availability and Failover management |
This use case relies on TrackMe’s SOAR integration and the Splunk App for SOAR integration, it monitors the status of Automation Brokers and can automatically update SOAR Assets as needed when Automation Brokers are detected as inactive, this provides automated High Availability and failover capabilities for SOAR Automation Brokers via TrackMe’s integration. |
|
Monitor the status of SOAR forwarding to Splunk |
This use case relies on Splunk indexed data to detect if there any issues with SOAR embedded forwarding to Splunk, it monitors for containers indexed in Splunk and would ideally be used in conjunction with the SOAR Timer App to regularly create health check containers based on an ingest interval. |
These use cases are provided via the Flex Object use cases library, but not that you can also manually implement new use cases, or customise builtin use cases as needed.
You can review the use case details ahead of their creation in TrackMe with the following command:
| trackmesplkflxgetuc | search uc_vendor=Splunk uc_category=splunk_soar
2. Requirements for SOAR monitoring
SOAR Cloud & SOAR on-premise
TrackMe’s SOAR integration is compatible with both SOAR Cloud and SOAR on-premise deployments.
Splunk Application for SOAR integration
TrackMe’s integration for SOAR relies on the Splunk SOAR integration for Splunk provided by the Splunk App for SOAR:
Hint
Splunk App for SOAR
TrackMe performs active and bi-directional interactions with the SOAR API
TrackMe relies on the Splunk App for SOAR integration and connectivity definition to achieve this job
You do not need to have any additional configuration in TrackMe as long as the Splunk App for SOAR is installed and configured
Some of the SOAR use cases rely on the SOAR events indexed in Splunk (index-phantom_*) which is also part of the Splunk App for SOAR integration
TrackMe leverages the Splunk App for SOAR and extends its capabilities even further
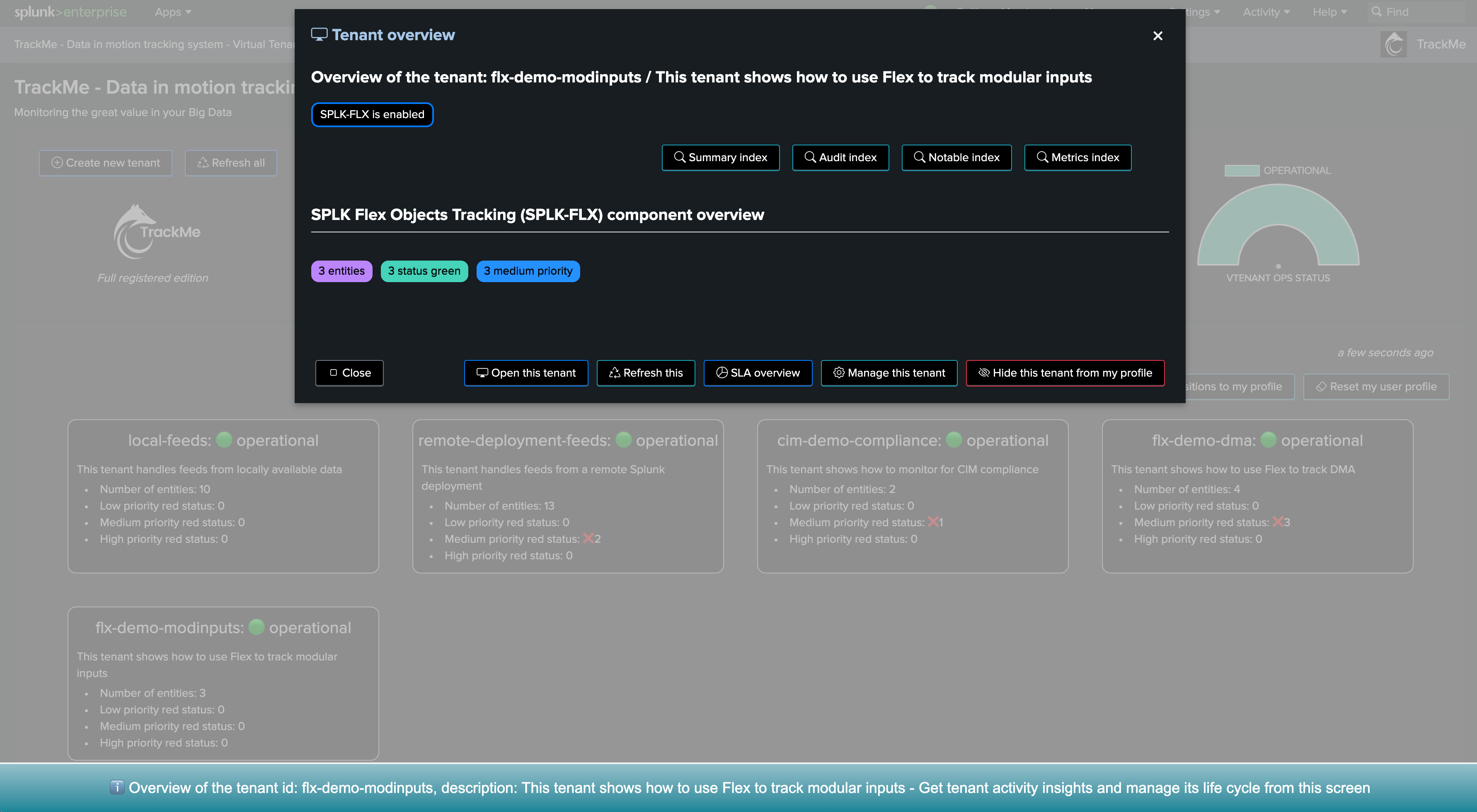
TrackMe tenant with the Flex Object component for SOAR
You need a TrackMe tenant with the Flex Object component enabled, you can decide to create a dedicated tenant for the monitoring of SOAR, and use any existing tenant of your choice.
Once the Flex trackers have been created, TrackMe automatically groups the resulting entities for SOAR into the following groups:
uc_ref |
grouping |
|---|---|
splk_soar_actions_apprun_failures, splk_soar_actions_playbooks_failures |
Splunk_SOAR:actions_health |
splk_soar_assets_health |
Splunk_SOAR:asset_health |
splk_soar_infra_load, splk_soar_services_health |
Splunk_SOAR:infrastructure |
splk_soar_services_health |
Splunk_SOAR:services_health |
splk_soar_automation_brokers_manage |
Splunk_SOAR:automation_broker_manage |
TrackMe deployment target
In TrackMe, you can choose where the SOAR monitoring Flex Objects use cases are executed, this can be either “local” or a remote deployment.
Note that some of the use cases would require TrackMe to be deployed on the remote target, as well as the Splunk App for SOAR configured on the remote target.
3. Implementation of SOAR monitoring
3.1 Integration architecture overview
The following diagram represents the integration from an high level perspective:
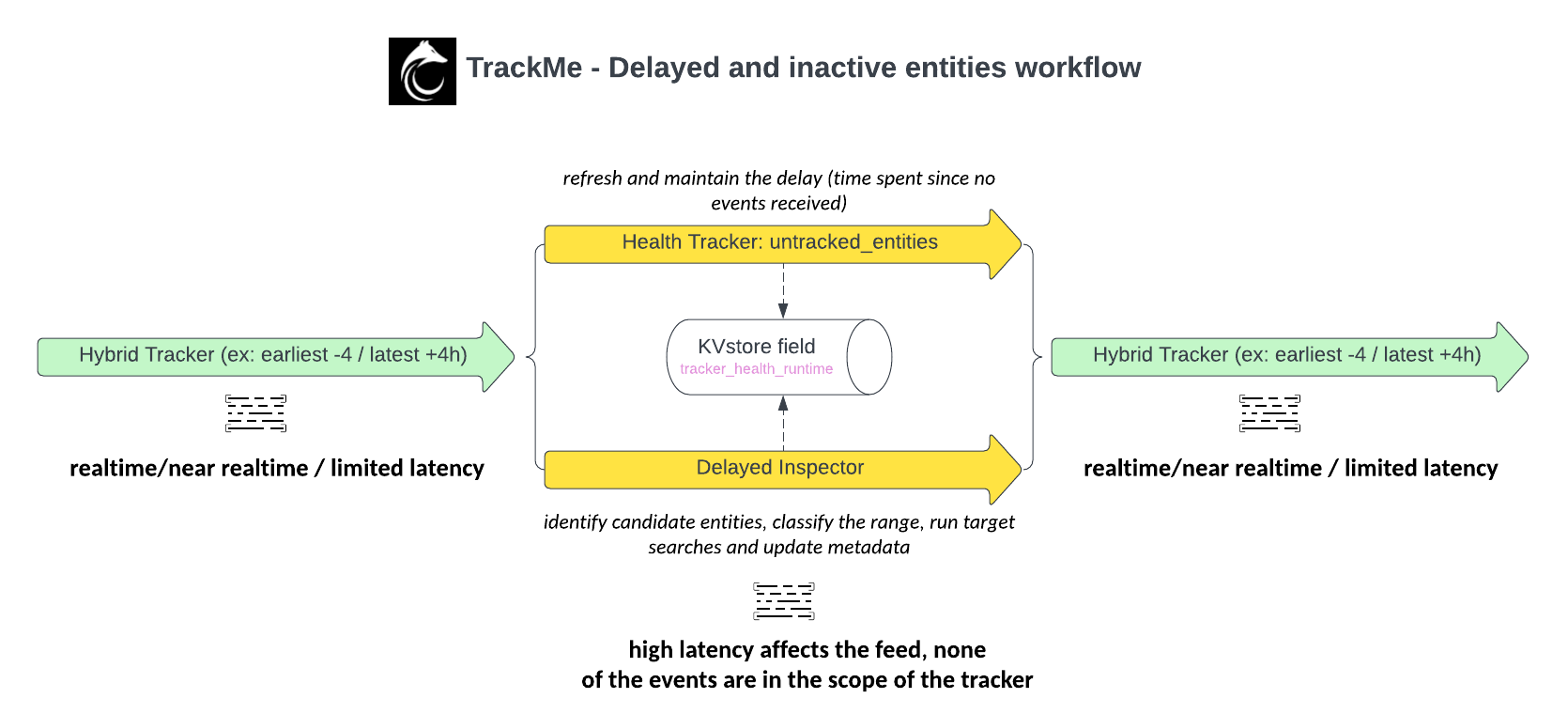
As a brief summary:
REST API related use cases in TrackMe imply an active interaction with SOAR API
TrackMe retrieves and loads the SOAR account configuration from the Splunk App for SOAR, you do not need to define anything in TrackMe
TrackMe implements its own REST queries against the SOAR API as needed, in some cases such as the Assets connectivity check, this interaction may imply a bi-directional integration with POST and GET calls performed by TrackMe
Some other use cases only deal with the SOAR data indexed in Splunk, and do not imply an API interaction
3.2 Creating SOAR Flex Object trackers
Hint
Running actions on a remote Splunk Search Head tier
You can leverage TrackMe’s splunkremotesearch to run these actions transparently on a remote Splunk Search Head tier
In this case, the Splunk App for SOAR would be installed and configured on the target (not on TrackMe’s Search Head)
However, TrackMe needs to be be installed on the target Splunk Search Head tier, although it is unconfigured and not actively running anything (if you run in Splunk Cloud Victoria, TrackMe is installed on all Search Heads automatically)
You need to create a TrackMe remote account which uses a token related a Splunk user on the remote Search Head
TrackMe leverages a minimalist least privileges approach, the user on the remote Search Head tier only needs to be a member of the power role and trackme_admin role (or have equivalent capabilities)
This requires TrackMe version 2.0.48 and later as we have addressed some issues to allow minimal permissions to be used
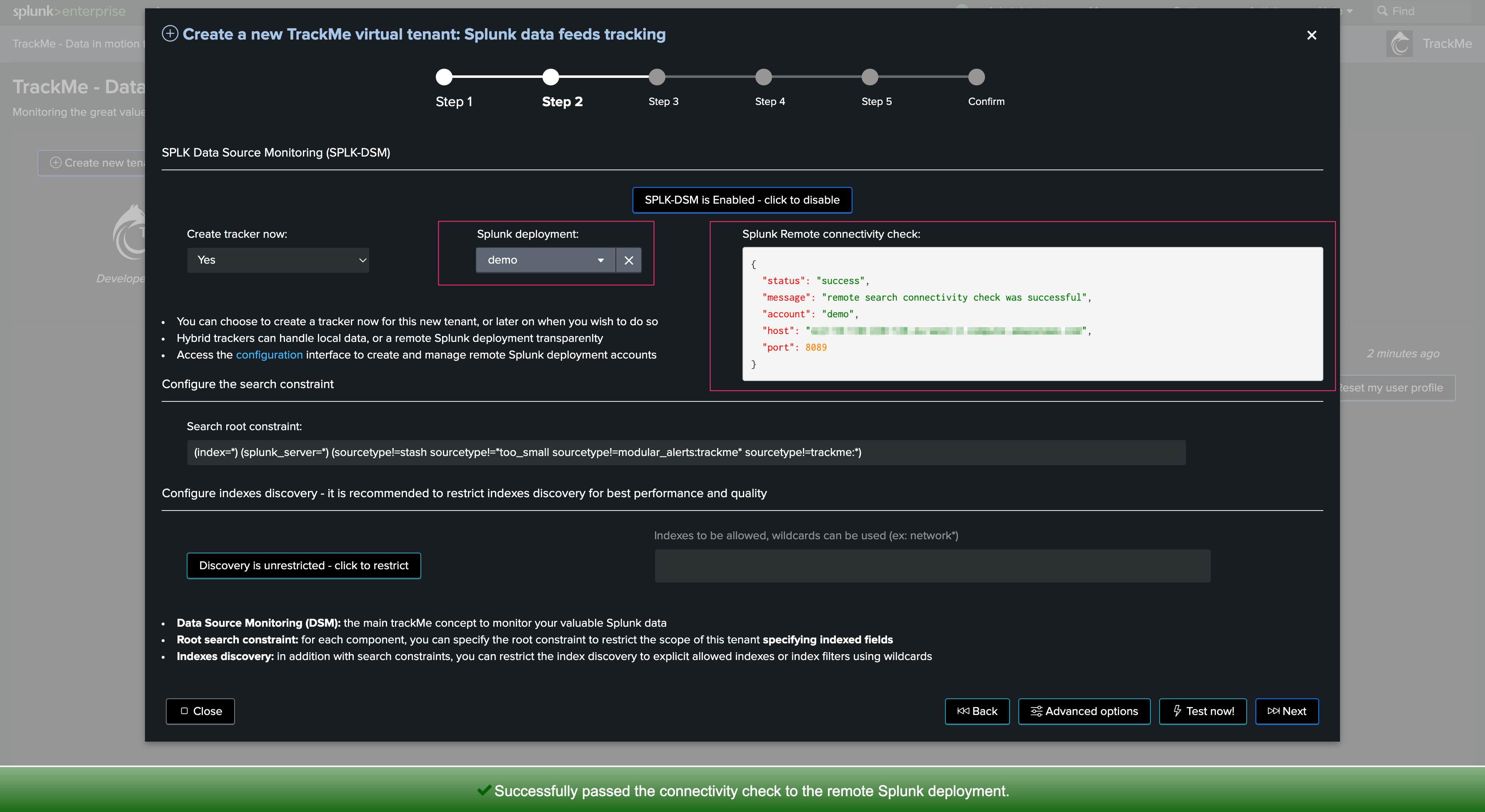
Once a TrackMe Virtual Tenant with the Flex Object (splk-flx) has been created, the setup is really straightforward and done via the UI:
Then click on Create a new Flex Tracker, select Splunk as the vendor and splunk_soar as the category, the next step is to review and validate the results, this is all:
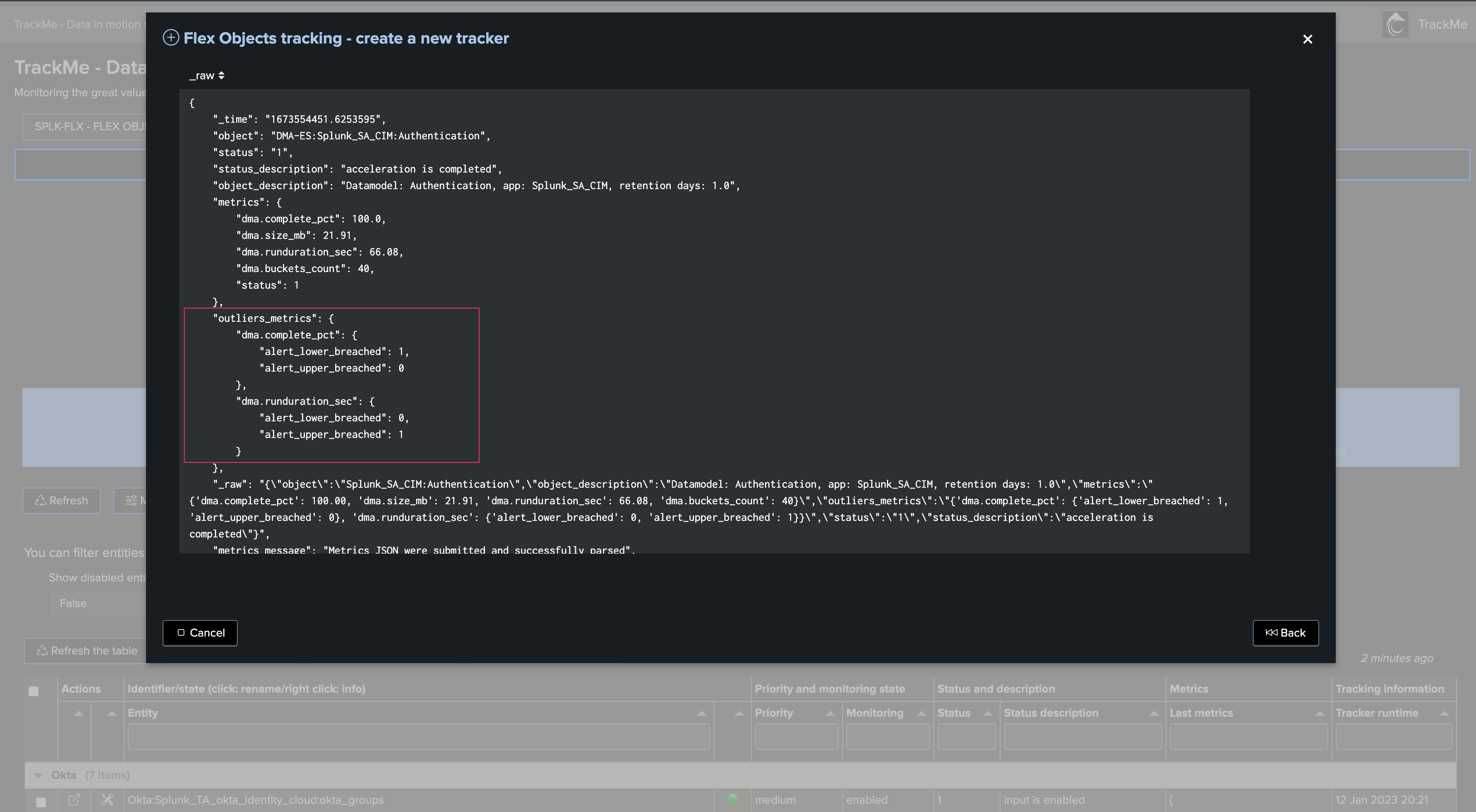
Example of results with the Assets active health check:
This asset is failing the connectivity check:
This asset passes successfully:
Setup is completed, the number of resulting entities depends on your environment:
4. SOAR Connectors Assets status active health check
A key monitoring capability for SOAR is to be able to detect as soon as possible when an application and its corresponding asset is experiencing an issue.
An asset that fails the status health check means that actions cannot be performed anymore, either ad-hocs actions requested by analysts or automated actions in the context of SOAR Playbooks.
Failures can happen for a variety of reasons, such as service accounts credential expiration, firewall rules changes or loss, API changes, SOAR Application upgrades, and many more.
This is an highly critical aspect of SOAR monitoring, especially true as Playbooks will only execute an action when needed, so the Application integration failure could remain undetected before it’s too late.
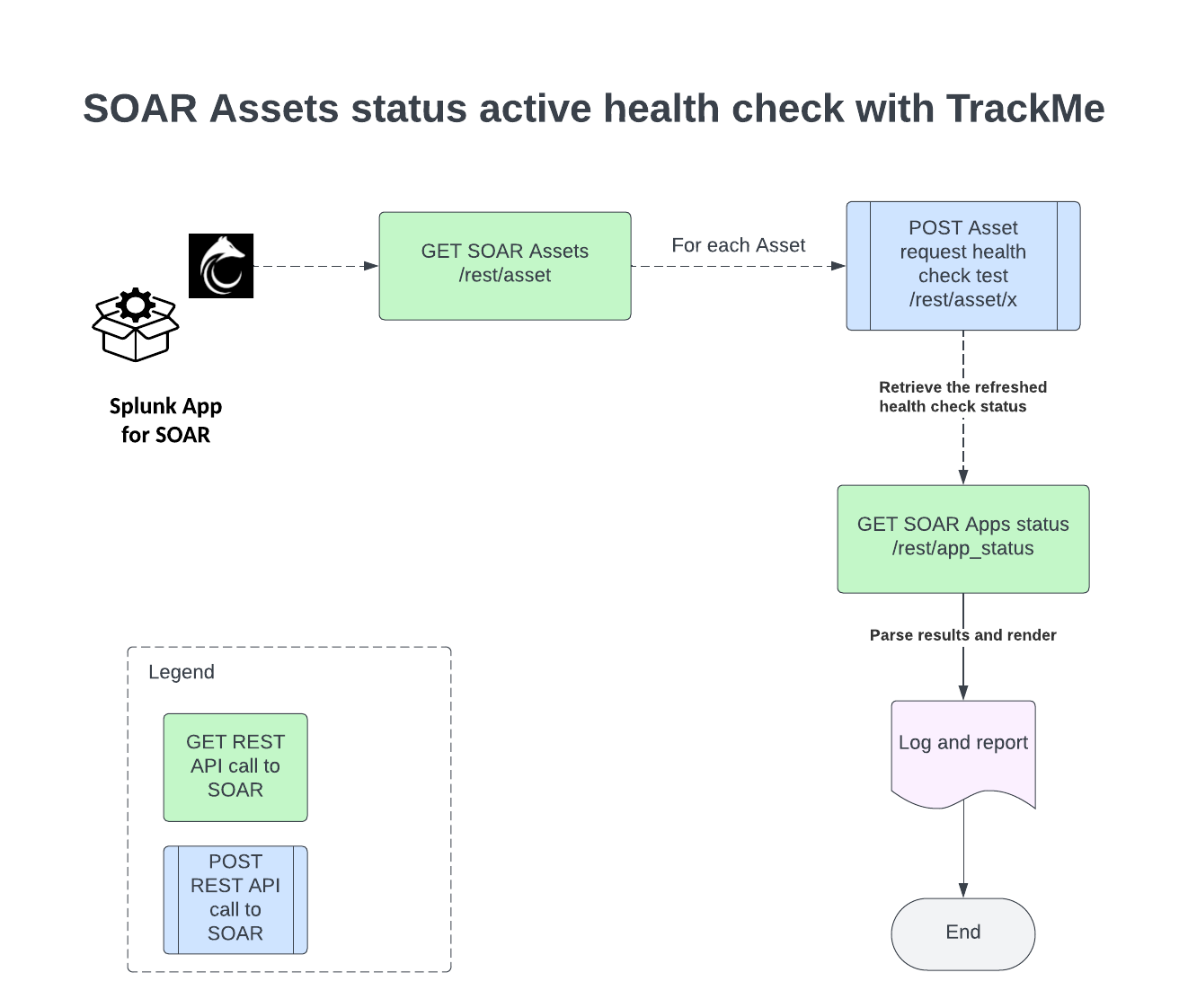
SOAR has a builtin and mandatory connectivity feature per application, and per asset, however this health check is not continuously performed by SOAR, so only monitoring the /rest/app_status endpoint would result in monitoring outdated information.
TrackMe handles this task by performing a multi-steps bi-directional integration with the SOAR REST API, summarised in the following diagram:
Advanced pre-built bi-directional interactions with Assets active check
The SOAR Assets active check in TrackMe relies on some multi-steps and bi-directional actions performed by TrackMe, the default usage of the command is the following:
| trackmesplksoar soar_server=* action=soar_test_apps action_data="{\"active_check\": \"True\", \"assets_allow_list\": \"None\", \"assets_block_list\": \"None\"}"
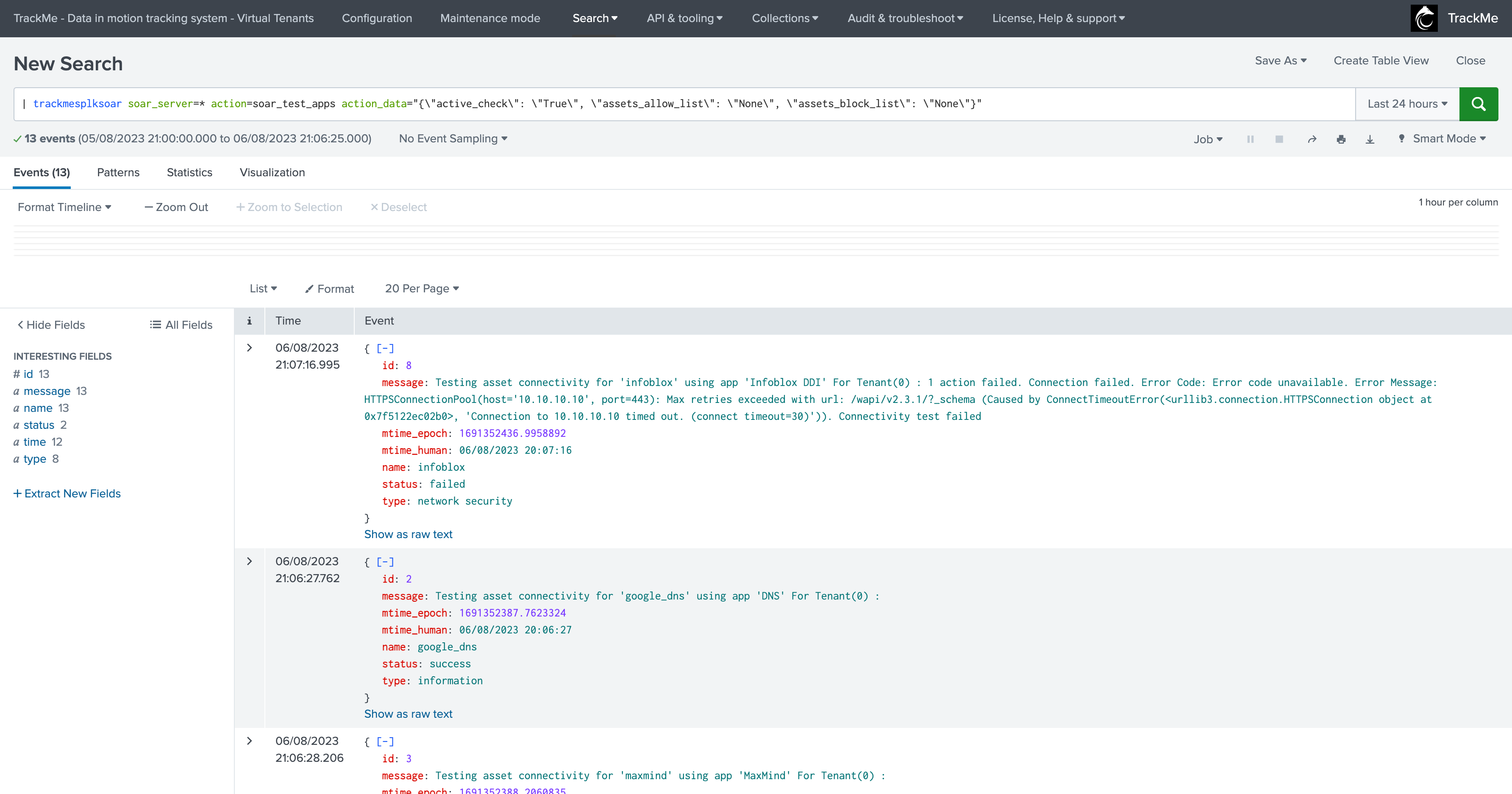
In summary, the command does the following:
Retrieve the list of assets eligible for a connection test
For each asset, perform a POST call against the Asset API endpoint which requests an immediate application health check
Record the response and store for later usage in the process
Retrieve the Asset app_status endpoint result, parse and render the final results
The command can accept several options:
Active checks
The default behaviour with active_check: True means TrackMe will actively perform the check bu running the POST call as described above:
If disabled with active_check: False, TrackMe does not perform the POST call and instead relies on SOAR doing it once per day, therefore it can take up to 24 hours before a failing application could be detected.
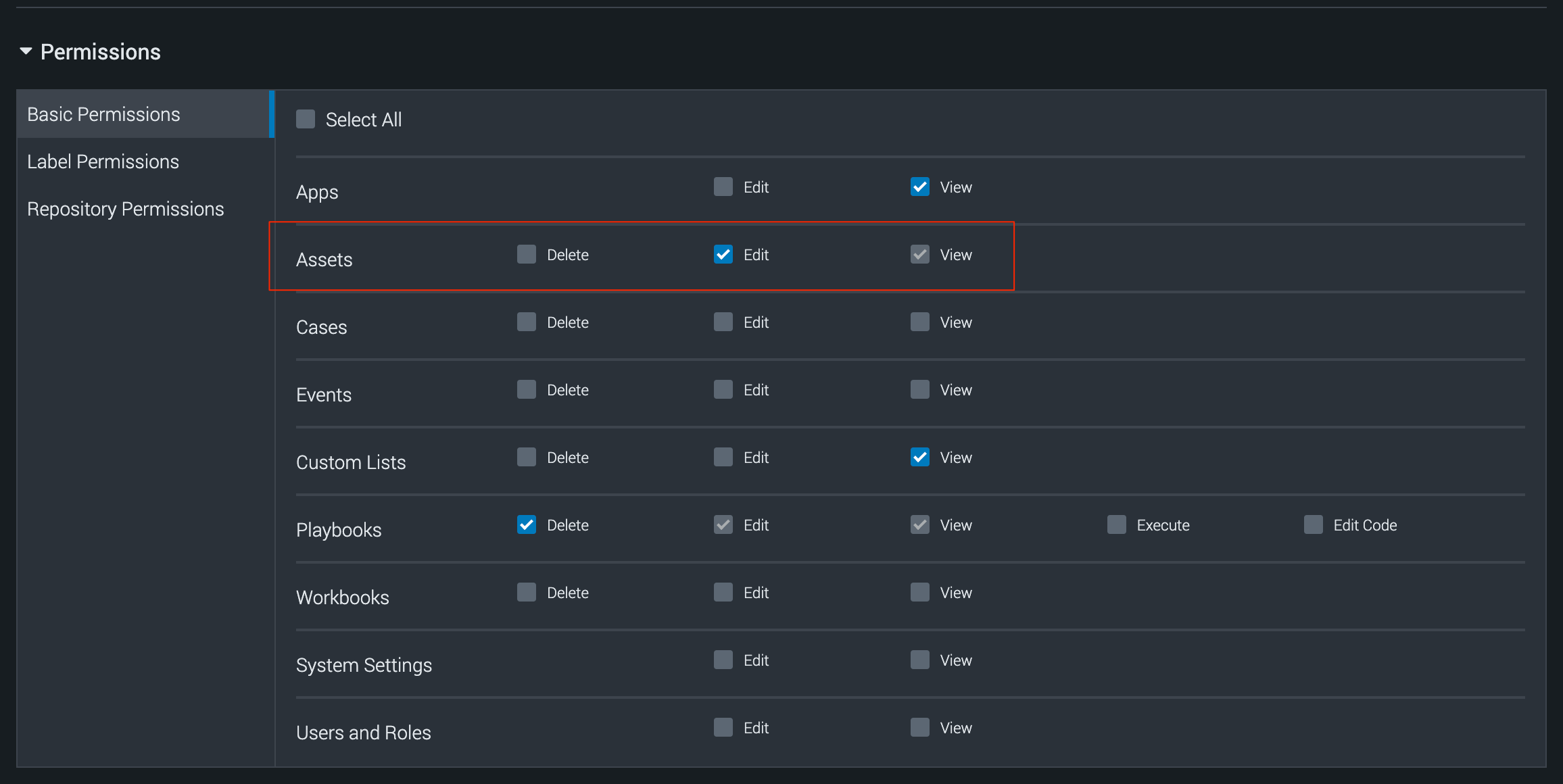
Note that active_check: True requires the SOAR automation user to have the edit Assets permissions:
Allow list and Block list:
You can mix the usage of asset_allow_list and asset_block_list to restrict and/or avoid some assets from being taken into account, for instance to avoid including the SMTP asset “internal_smtp”:
| trackmesplksoar soar_server=* action=soar_test_apps action_data="{\"active_check\": \"True\", \"assets_allow_list\": \"None\", \"assets_block_list\": \"internal_smtp\"}"
5. SOAR Automation Brokers Monitoring, High Availability and Failover with TrackMe
Hint
Automation Broker Pools: Latest updates since TrackMe 2.1.8
This feature was first introduced in TrackMe Version 2.0.50.
Since TrackMe 2.1.8, these capabilities were enhanced so we can support independent pools of brokers that can be defined and managed in TrackMe.
This allows you to have full flexibility, and configure multiple groups of brokers where Assets can be moved transparently depending on the brokers availability.
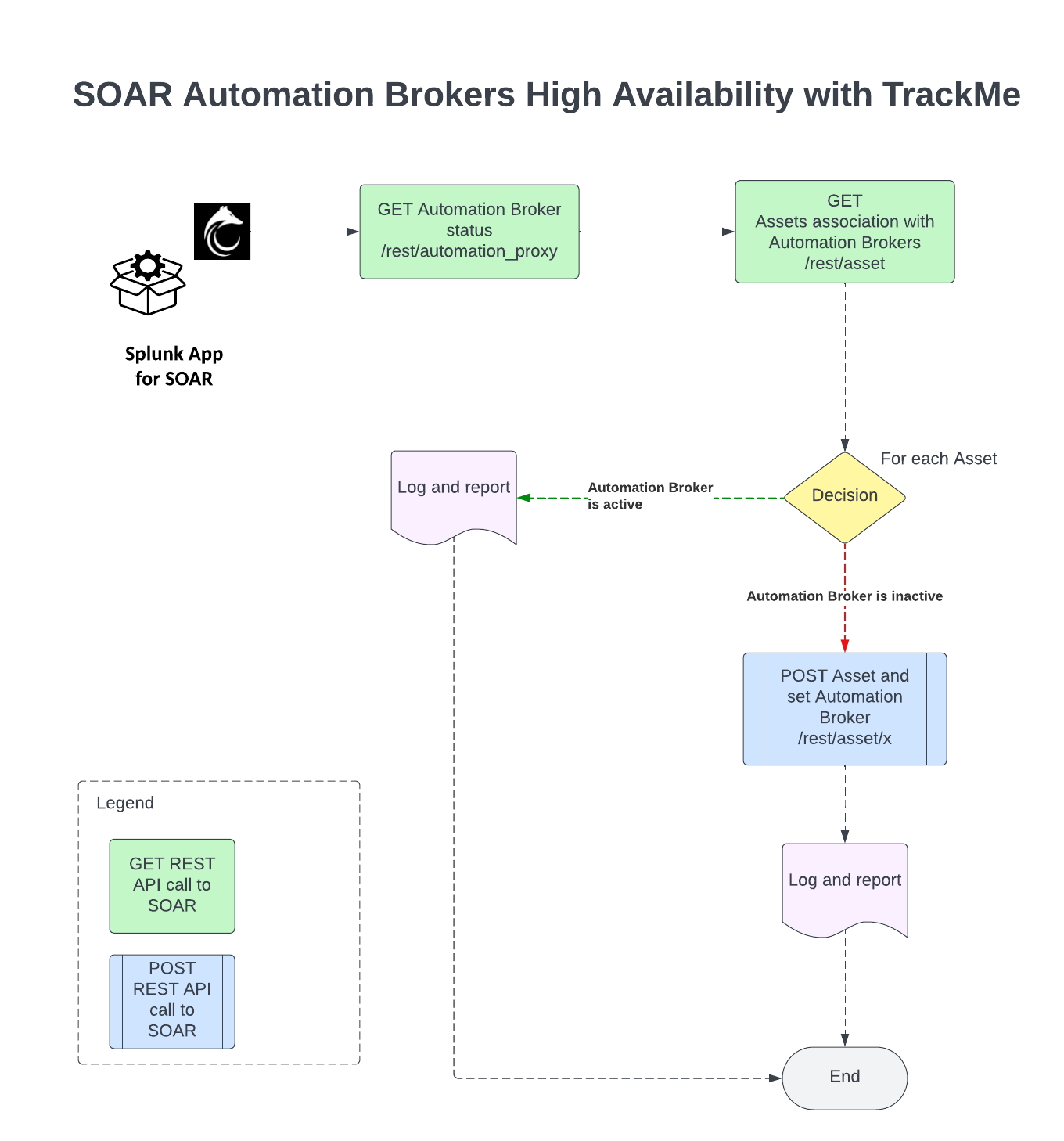
The builtin use case splk_soar_manage_automation_brokers allows managing SOAR Automation Brokers High Availability using TrackMe, based on the following workflow:
Retrieve the list of Automation Brokers and their status from the SOAR API
Retrieve the list of SOAR Assets and the association with Automation Brokers
For each Automation Broker, if the broker status is inactive, perform an update of associated Assets to the next available and online Automation Broker
Automation broker status: the status is provided by the SOAR API and is based on the health check performed automatically by the SOAR Automation Broker.
Additional options can be used to control and restrict the High Availability features, consult the examples below.
High level workflow diagram:
5.1 Requirements
The SOAR Automation User requires Assets management permissions:

5.2 SOAR Automation Broker High Availability - failure detection and Assets updates
The tracking and management of SOAR Automation Brokers is achieved by running the following command through the builtin use case splk_soar_manage_automation_brokers:
| trackmesplksoar soar_server=* action=soar_automation_broker_manage
The command calls the TrackMe REST API endpoint /services/trackme/v2/splk_soar/admin/soar_automation_broker_manage, the following options are available:
argument |
description |
|---|---|
|
The SOAR server account as defined in the Splunk App for SOAR, if unspecified or set to *, the first server in the Splunk application for SOAR configuration will be used |
|
Optional, the run mode, valid options are readonly | live. In read only mode, the Asset is not updated and only the message of the action to be performed is registered. In Live mode, assets are updated if the associated broker is not healthy, and if at least one active broker is available in the pool, defaults to live |
|
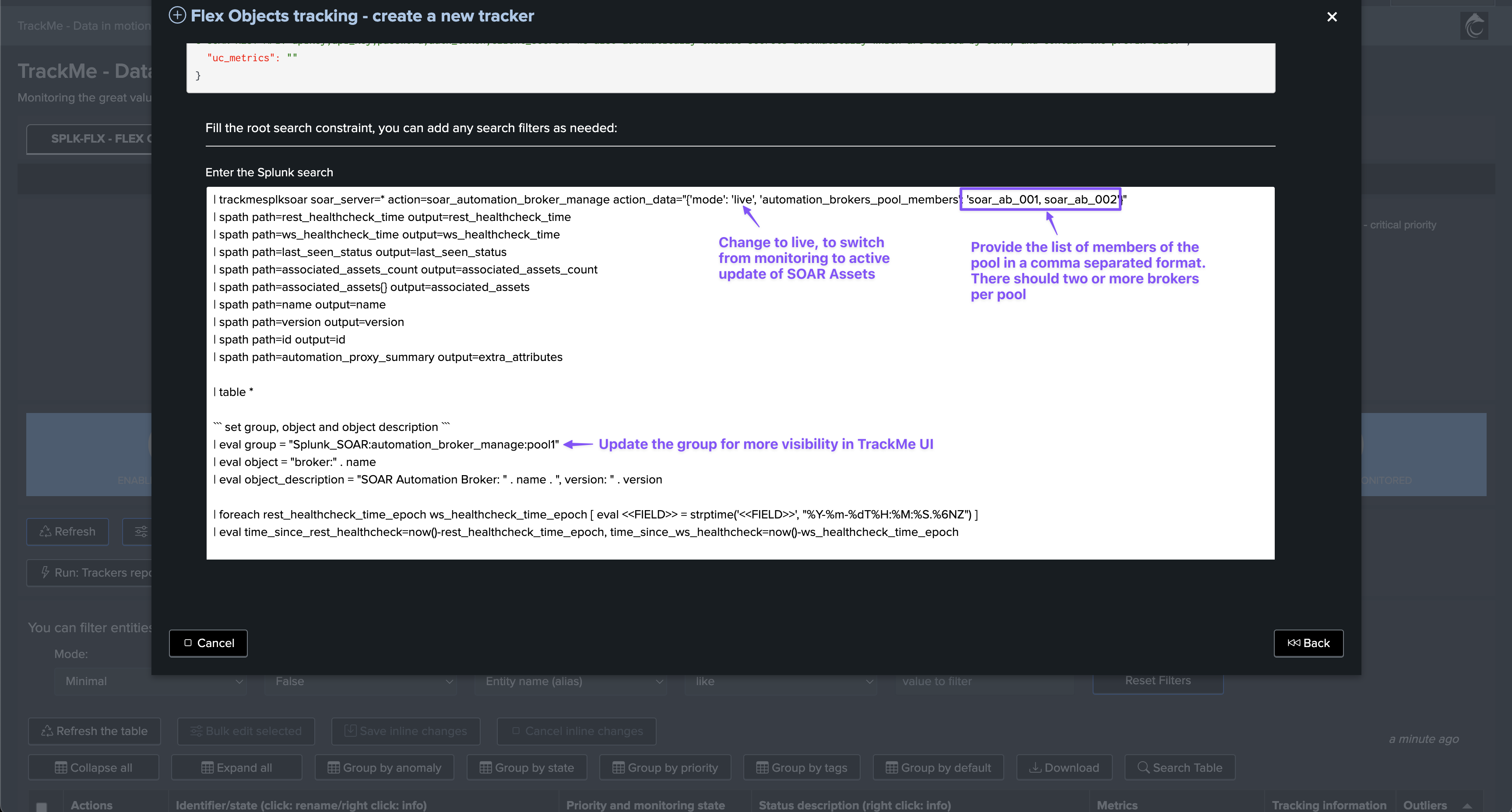
The comma separated list of Automation Brokers for the pool, if unspecified TrackMe will consider all registered SOAR Automation Brokers. When specified, the Flex Object tracker instance is tight to a certain list of Automation Brokers, and only these will be considered for the High Availability management. When creating multiple Trackers to manage different pools, you can update the group definition to clearly separate the resulting TrackMe entities, for easier management in the TrackMe UI. |
Configuration example: Two pools of Automation Brokers
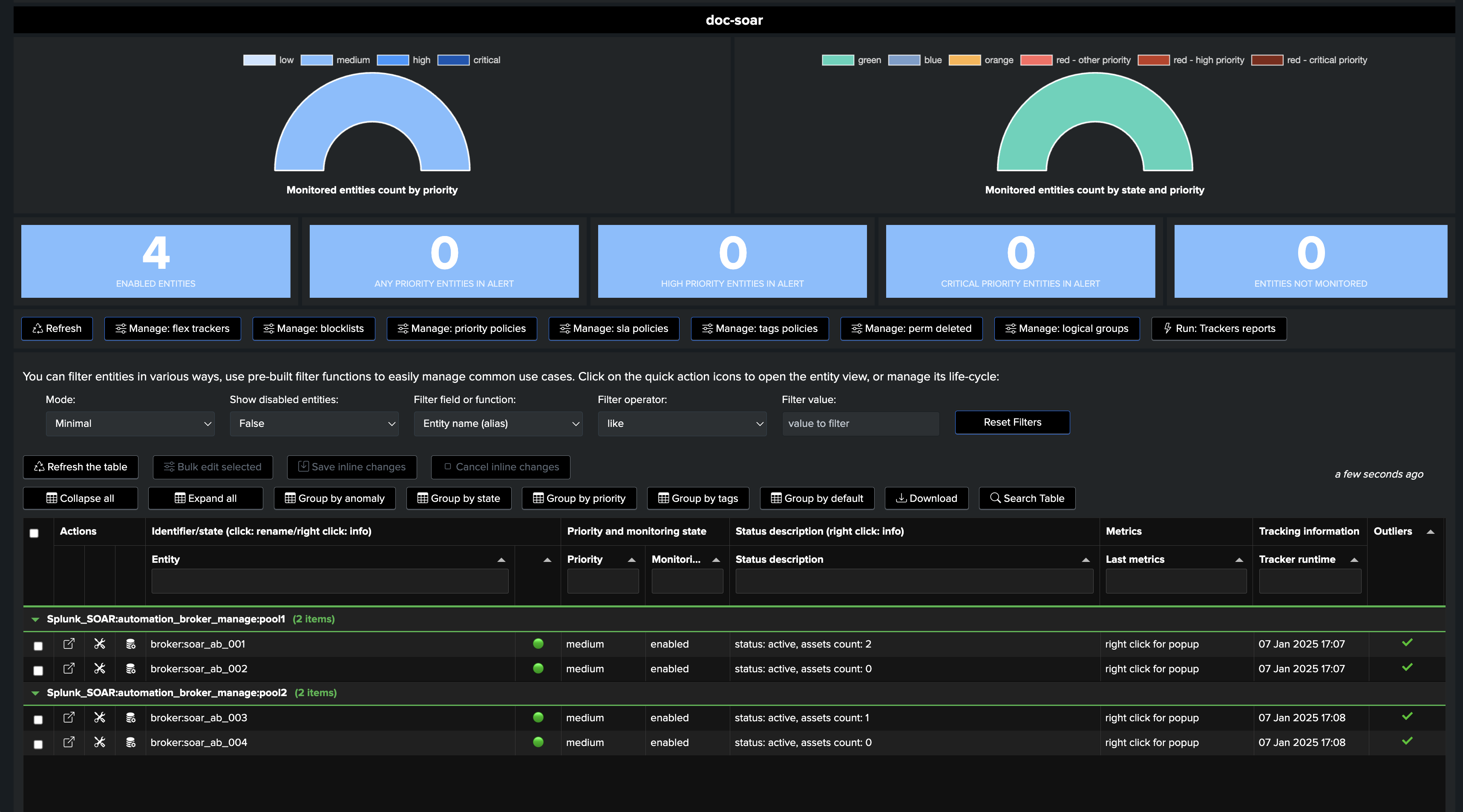
Consider the following Architecture scenario:
Our SOAR environment has 4 Automation Brokers in total.
Due to Network or any other technical constraints, certain assets can only use specific Automation Brokers.
Therefore, we have 2 groups of Automation Brokers, in each of these groups, Assets cab be configured to use either broker from that pool.
Automation Broker |
Pool |
|---|---|
soar_ab_001 |
Pool1 |
soar_ab_002 |
Pool1 |
soar_ab_003 |
Pool2 |
soar_ab_004 |
Pool2 |
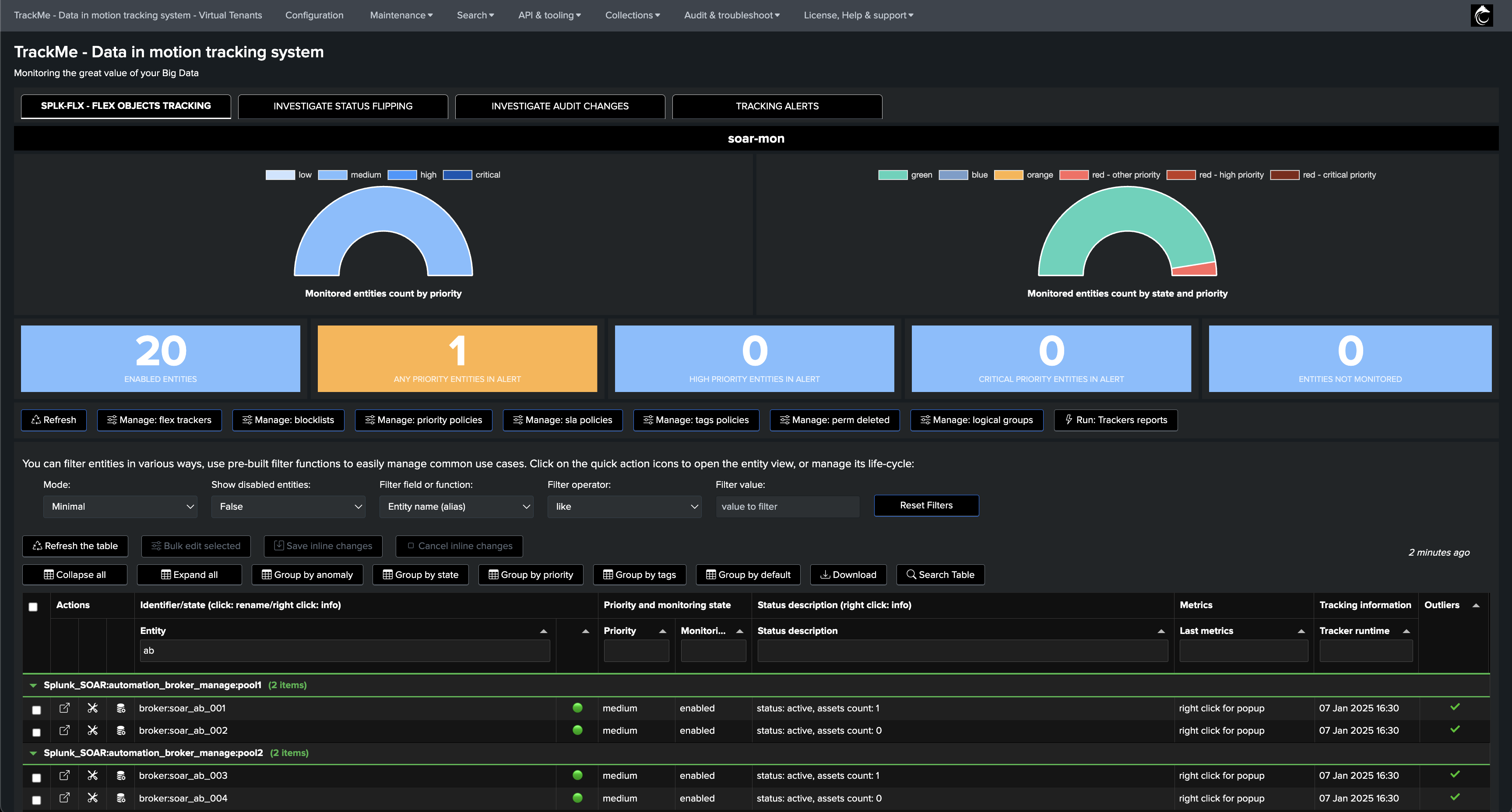
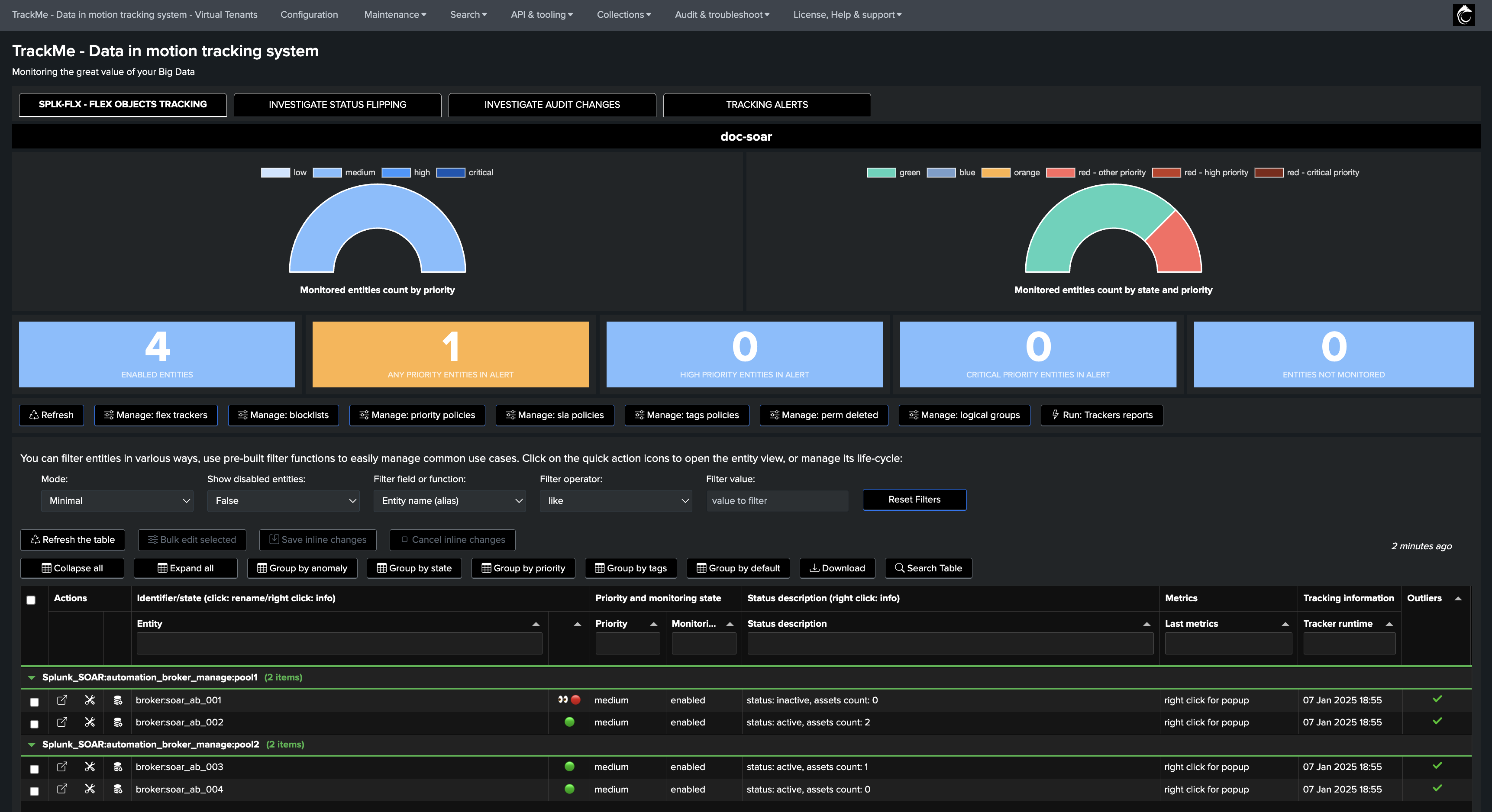
Create two Flex Object trackers to manage each pool:
Create the first Tracker as following, and repeat for the second pool:
Once the trackers have been executed at least once, our setup is ready and we have 4 entities representing the 2 pools of brokers:
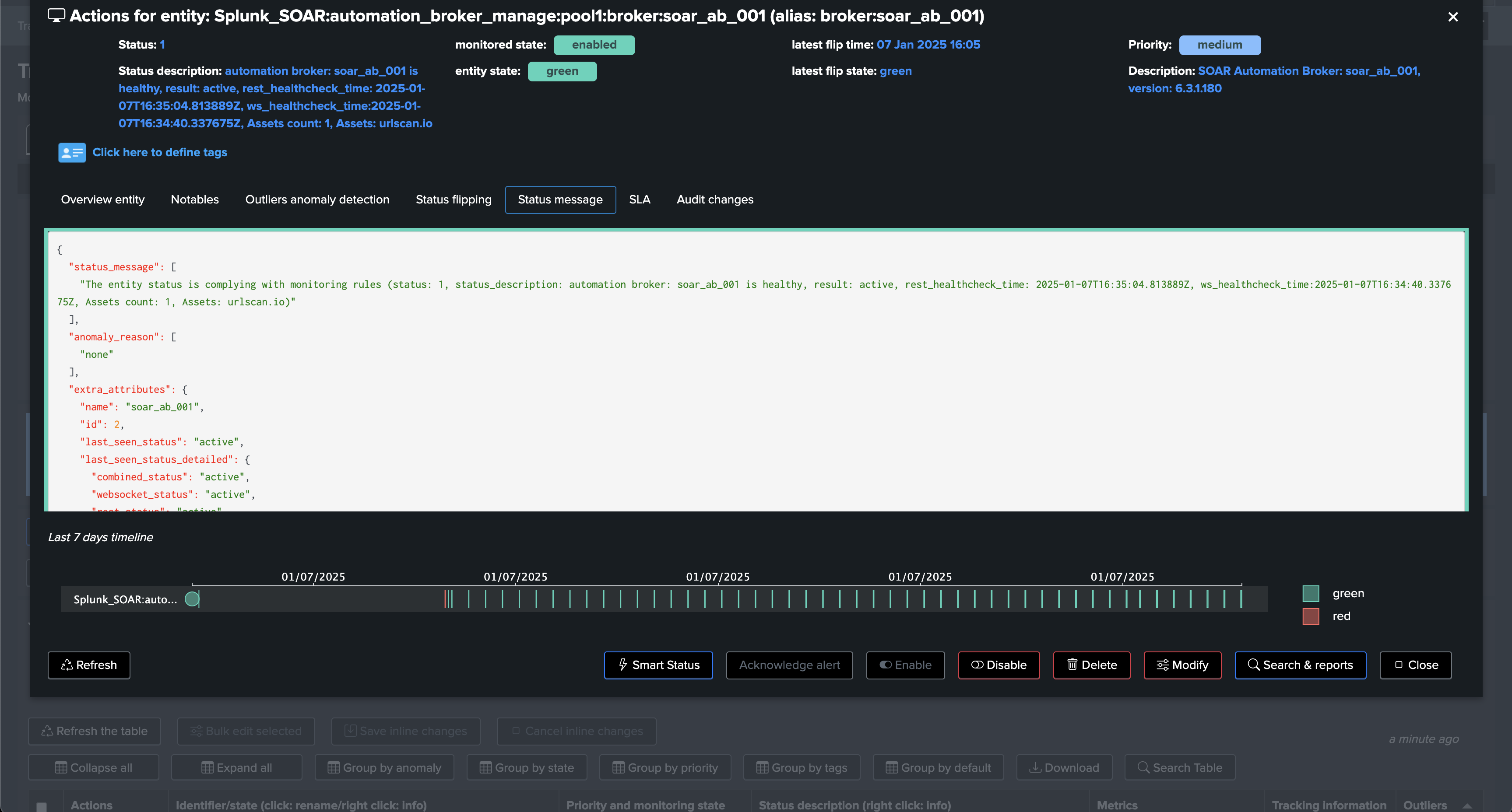
The status message shows the extended attributes, which contains all Metadata from the brokers, and various information such as the list of assets currently linked to this asset:
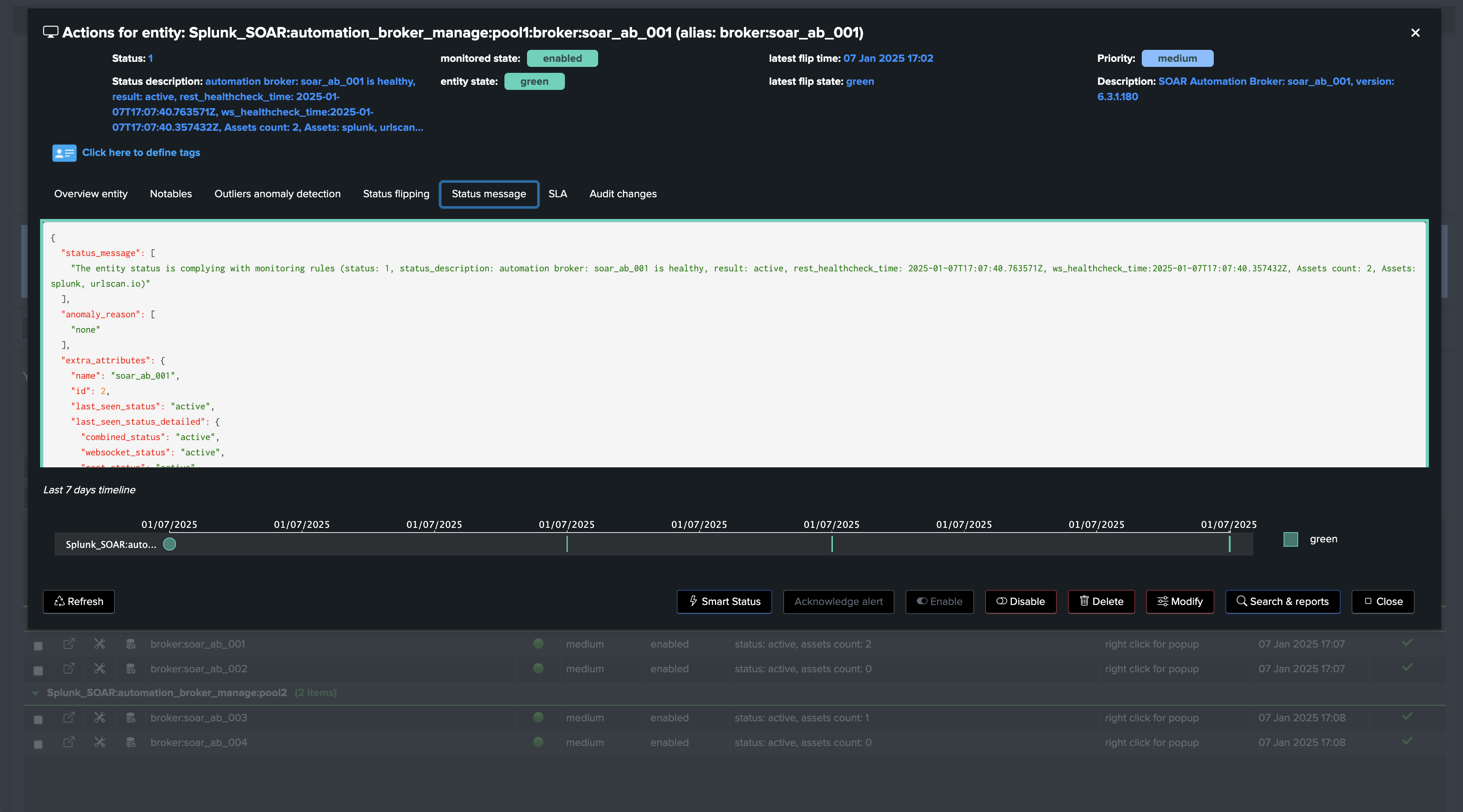
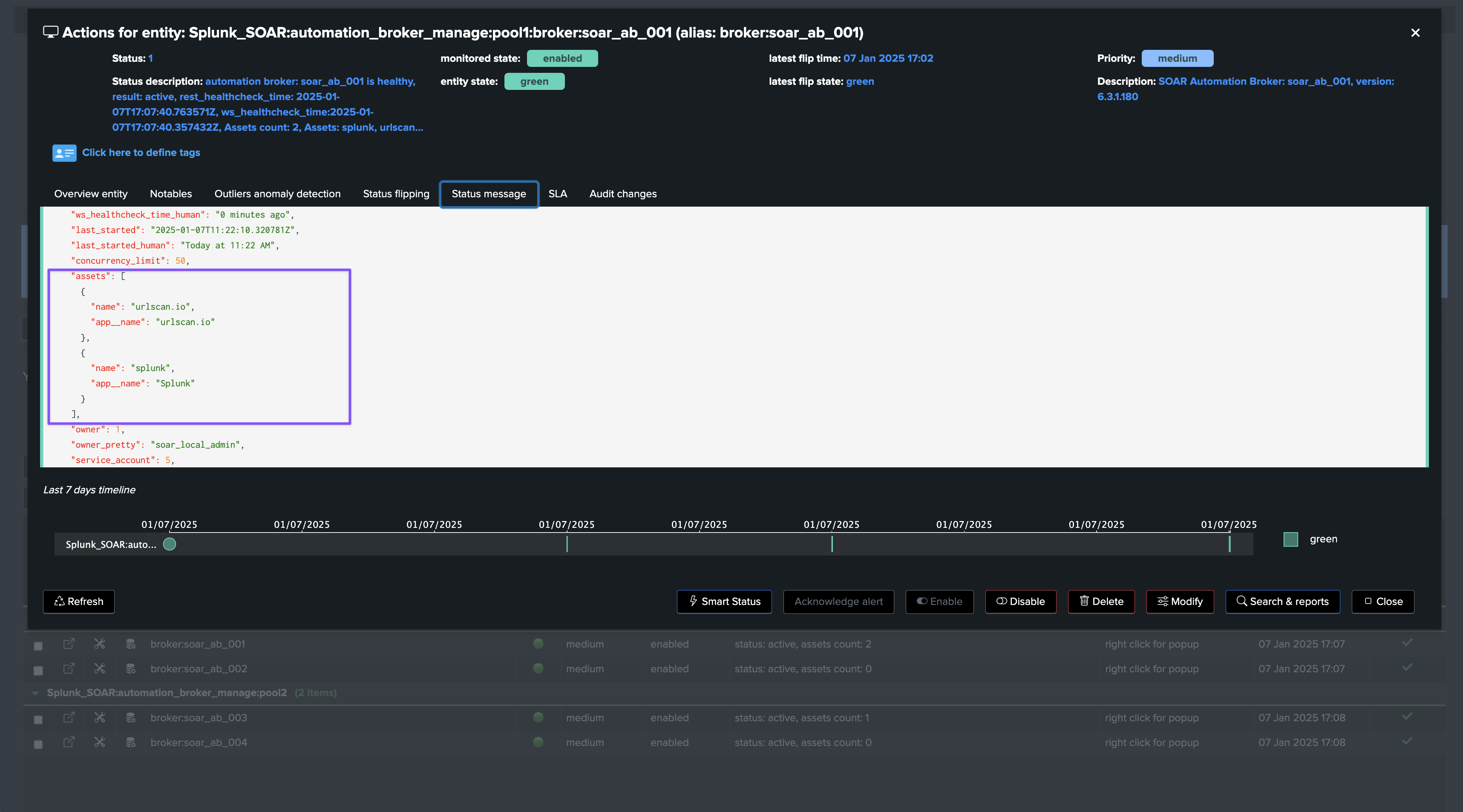
What happens when an Automation Broker is detected as inactive?
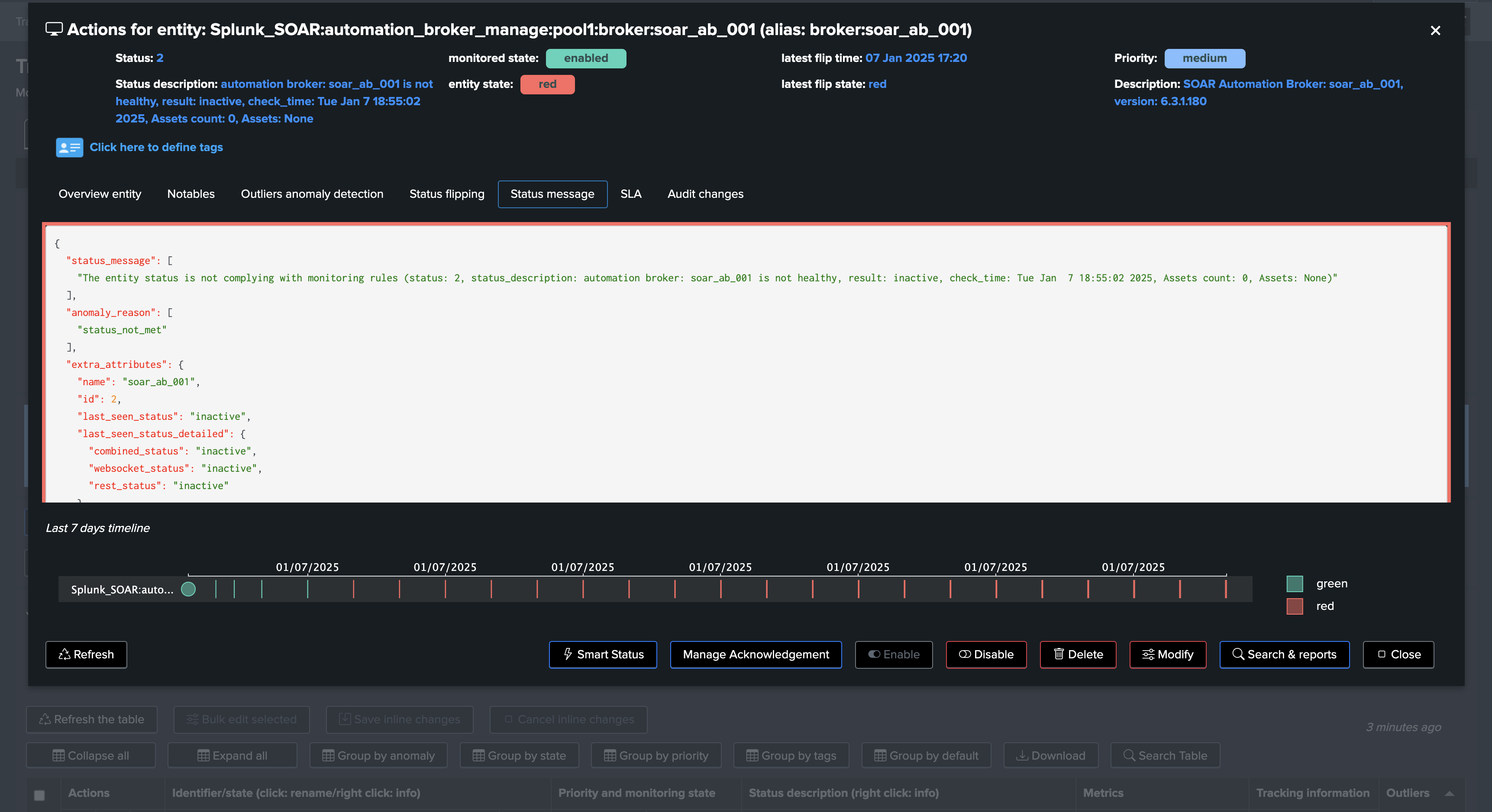
If an issue affects an Automation Broker, TrackMe turns the entity in red state, and will automatically update Assets so these are associated with any randomly chosen active broker from the same pool:
Logs can be found at:
index=_internal sourcetype=trackme:rest_api post_soar_automation_broker_manage
When updates of SOAR Assets are performed, the following search can be used to review the logs and executed actions:
index=_internal sourcetype=trackme:rest_api post_soar_automation_broker_manage updated

A typical trace for an Asset update will look the following example:
A first warning message shows that the Automation Broker associated with the Asset is currently offline, followed by the update result message from the action performed by TrackMe.
2025-01-07 17:20:06,002 WARNING trackme_rest_handler_splk_soar_admin.py post_soar_automation_broker_manage 1081 asset=urlscan.io, id=3 is associated with automation_broker=soar_ab_001, id=2, status=inactive, asset will be updated now!
2025-01-07 17:20:06,104 INFO trackme_rest_handler_splk_soar_admin.py post_soar_automation_broker_manage 1138 asset=urlscan.io, id=3, asset automation broker configuration was successfully updated from automation_broker=soar_ab_001, id=2, status=inactive to automation_broker=soar_ab_002, id=3, status=active, response="{'success': True, 'id': 3}"
What happens when the Automation Broker is back online?
When the Automation Broker is back online, the entity will turn back to green. However, note that the Asset definition will not be updated back to the original Automation Broker, this is a design choice to avoid a ping-pong effect, and to ensure that the Asset is always associated with an active Automation Broker.
6. Interacting with the SOAR API with GET and POST calls in pure SPL
The following sections show the root searches and technical details of each TrackMe’s SOAR use cases.
Refer to the SOAR API reference documentation as needed:
6.1 Running GET calls to SOAR API
trackmesplksoar:
TrackMe comes with a custom command (generating custom command) called trackmesplksoar, this SPL command does the interface with the Splunk App for SOAR and the SOAR API itself, usage:
| trackmesplksoar soar_server=<soar_server> action=<action> action_data=<json action data>
The command handles different options:
Syntax:
soar_server: the name of the SOAR server as configured in the Splunk App for SOAR
action: an action in the following support list:
soar_get|soar_post|soar_test_apps|soar_health_status|soar_health_memory|soar_health_load|soar_automation_broker_manageaction_data: a JSON formatted object, either used by specific actions or used to perform a POST query to a SOAR endpoint
Example: the following command allows retrieving the health information from the SOAR API, it targets the endpoint rest/health_status:
| trackmesplksoar soar_server=* action=soar_get action_data="{'endpoint': 'health'}" | spath
This action allows calling any SOAR API endpoint performing a GET call only.
Another example, to retrieve the configuration of all SOAR Assets, you would:
| trackmesplksoar soar_server=* action=soar_get action_data="{'endpoint': 'asset'}" | spath
6.2 Pre-built actions and advanced parsing
In some cases, such as the one above, it may not be very straightforward to parse and use the API endpoints results, for instance when there are nested JSON structures as part of the response.
For instance, for the ease of the integration, the custom command provides builtin use cases which will parse the JSON results as needed and render the results properly, for instance the following relies on the health endpoint and extracts the status of SOAR services:
| trackmesplksoar soar_server=* action="soar_health_status"
6.3 Performing a POST call to a SOAR API endpoint via TrackMe
In fact, you can perform a POST to a SOAR API endpoint using TrackMe’s integration, which the Splunk App for SOAR does not provide.
For instance, to run a POST against an Asset and request an immediate health check, you would first retrieve the list of assets to identify the ID of the Asset:
See:
https://docs.splunk.com/Documentation/SOAR/current/PlatformAPI/RESTInfo
https://docs.splunk.com/Documentation/SOAR/current/PlatformAPI/RESTAssets
| trackmesplksoar soar_server=* action=soar_get action_data="{'endpoint': 'asset'}" | spath
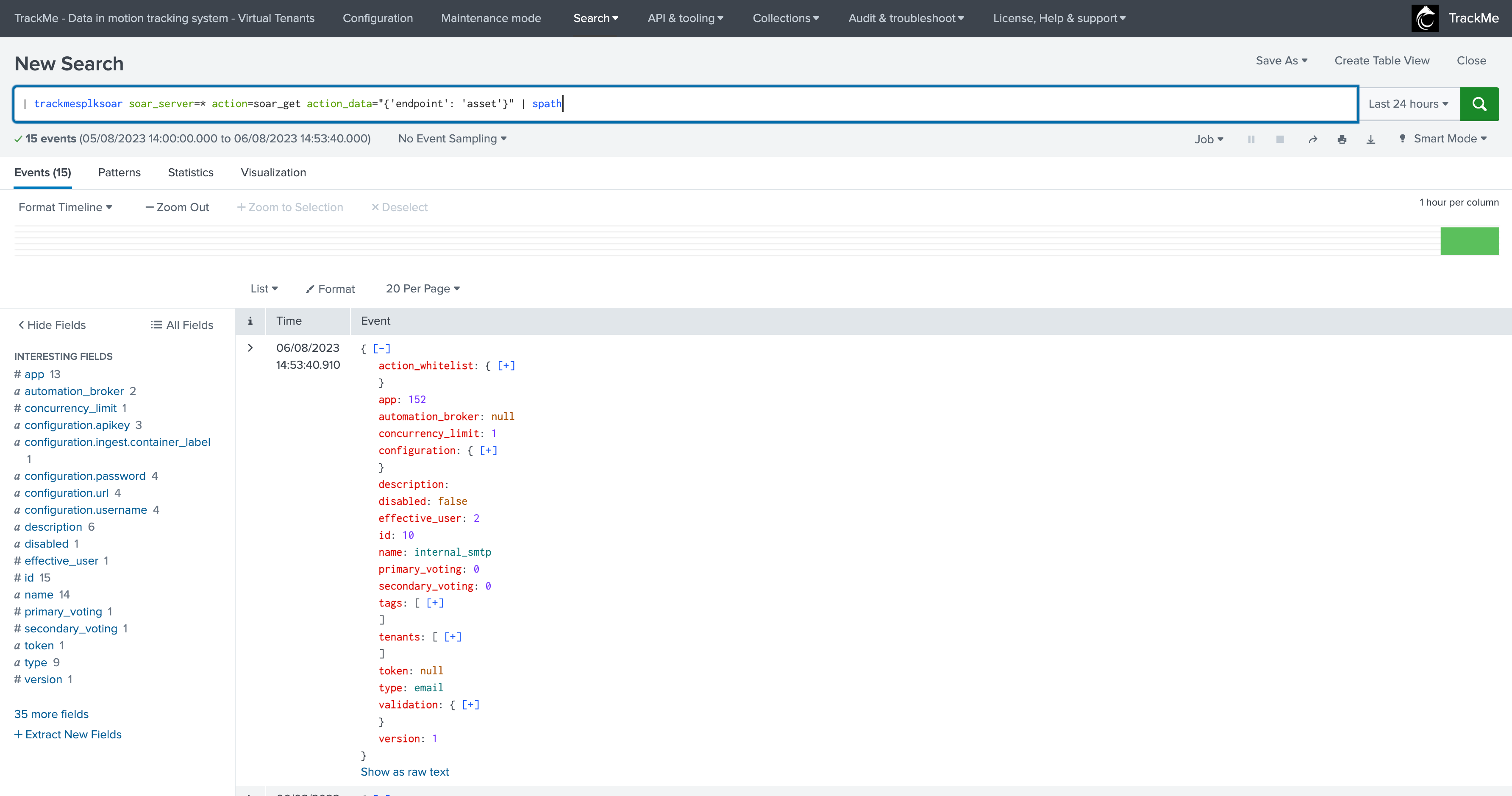
Then, you would:
| trackmesplksoar soar_server=* action=soar_post action_data="{'endpoint': 'asset/7', 'data': '{\"test\": \"true\"}'}"
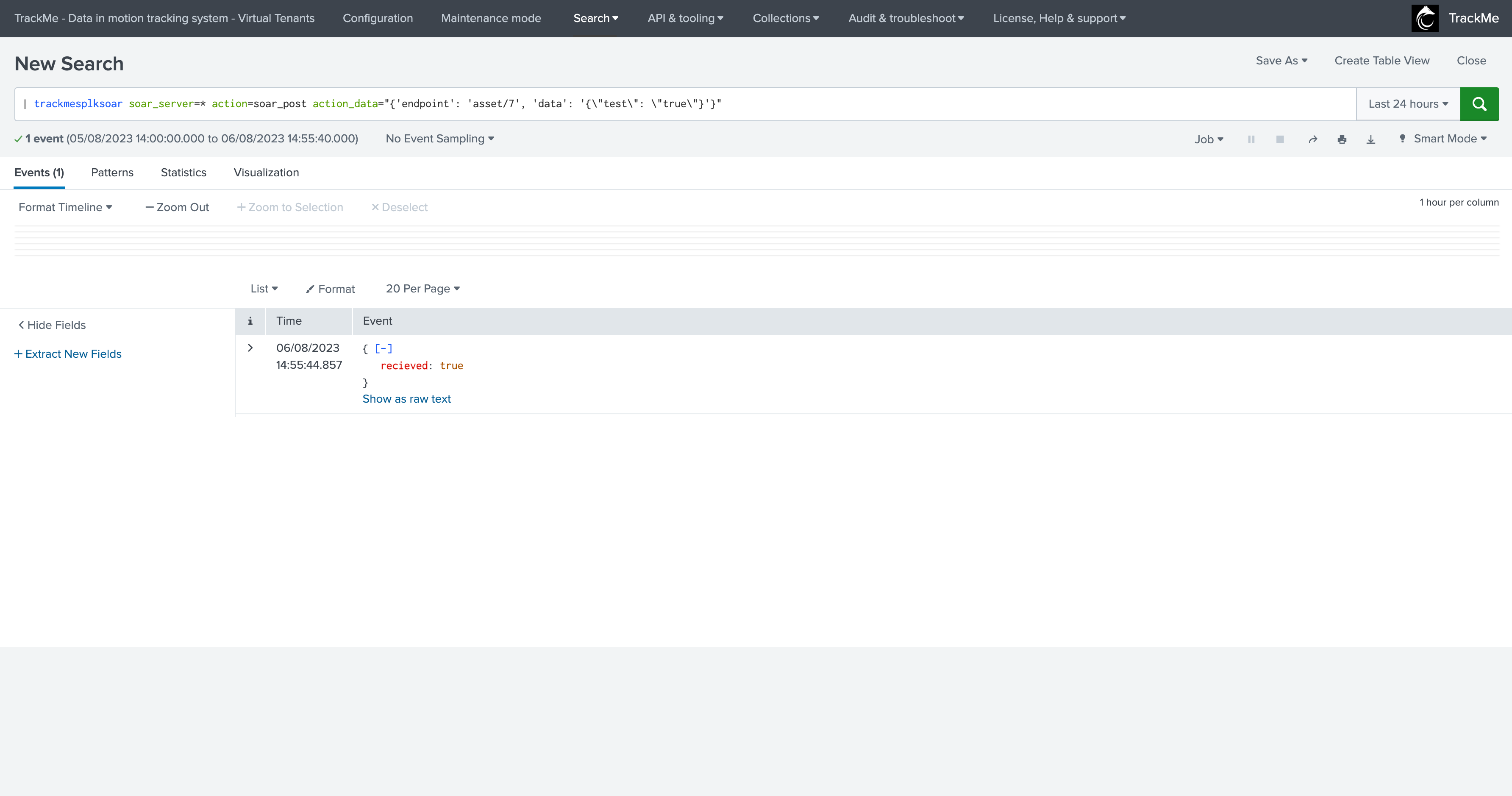
Note: “received: true” is the actual response from SOAR, this is not a typo from TrackMe but a typo in the SOAR API currently for this endpoint!
Another example, let’s request the sync refresh of a Git Repository via the SCM endpoint:
See:
First, we run a GET call to get the ID of the SCM Git repository configuration:
| trackmesplksoar soar_server=* action=soar_get action_data="{'endpoint': 'scm'}"
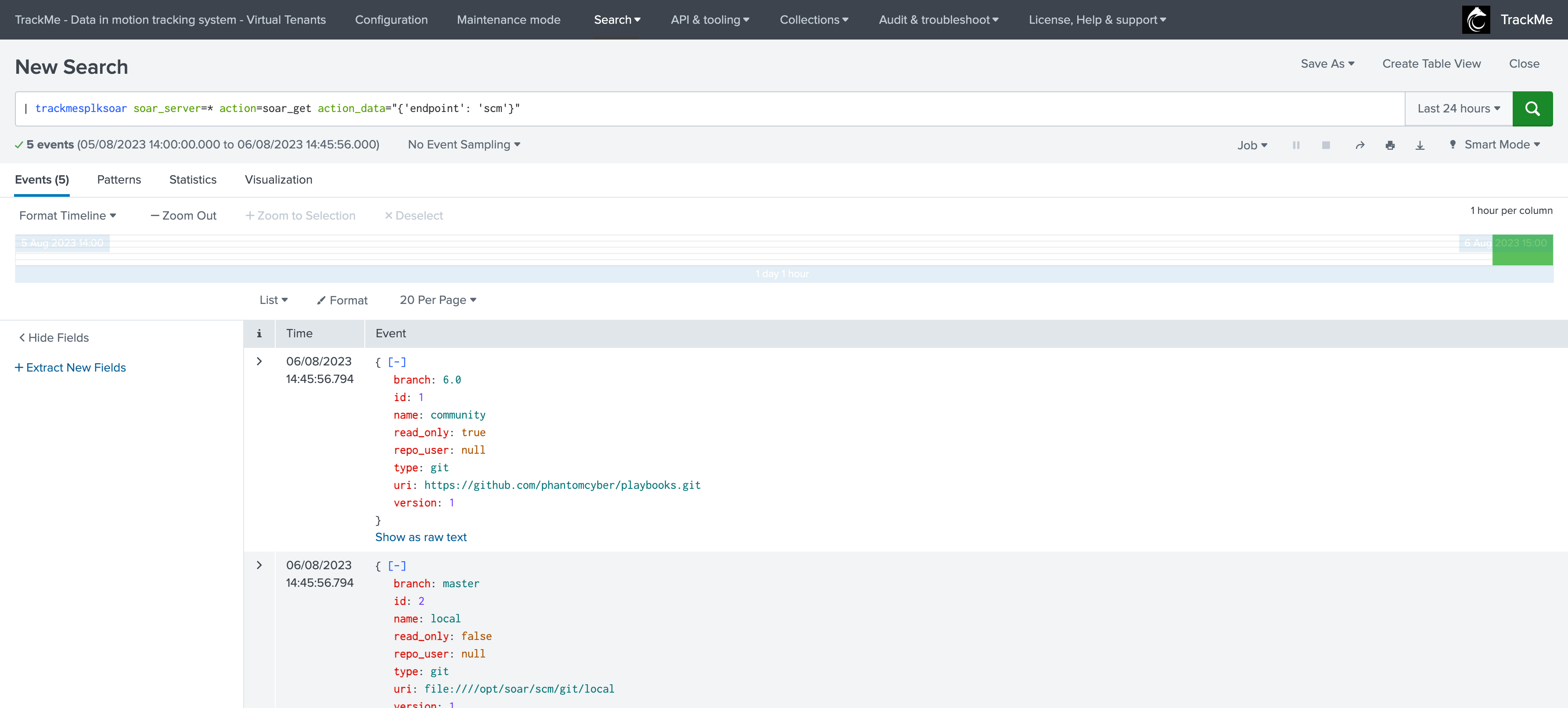
We run a POST call again to request the SCM update, we have a few changes that were actually merged to the branch:
| trackmesplksoar soar_server=* action=soar_post action_data="{'endpoint': 'scm/5', 'data': '{\"pull\": \"true\", \"force\": \"true\"}'}"
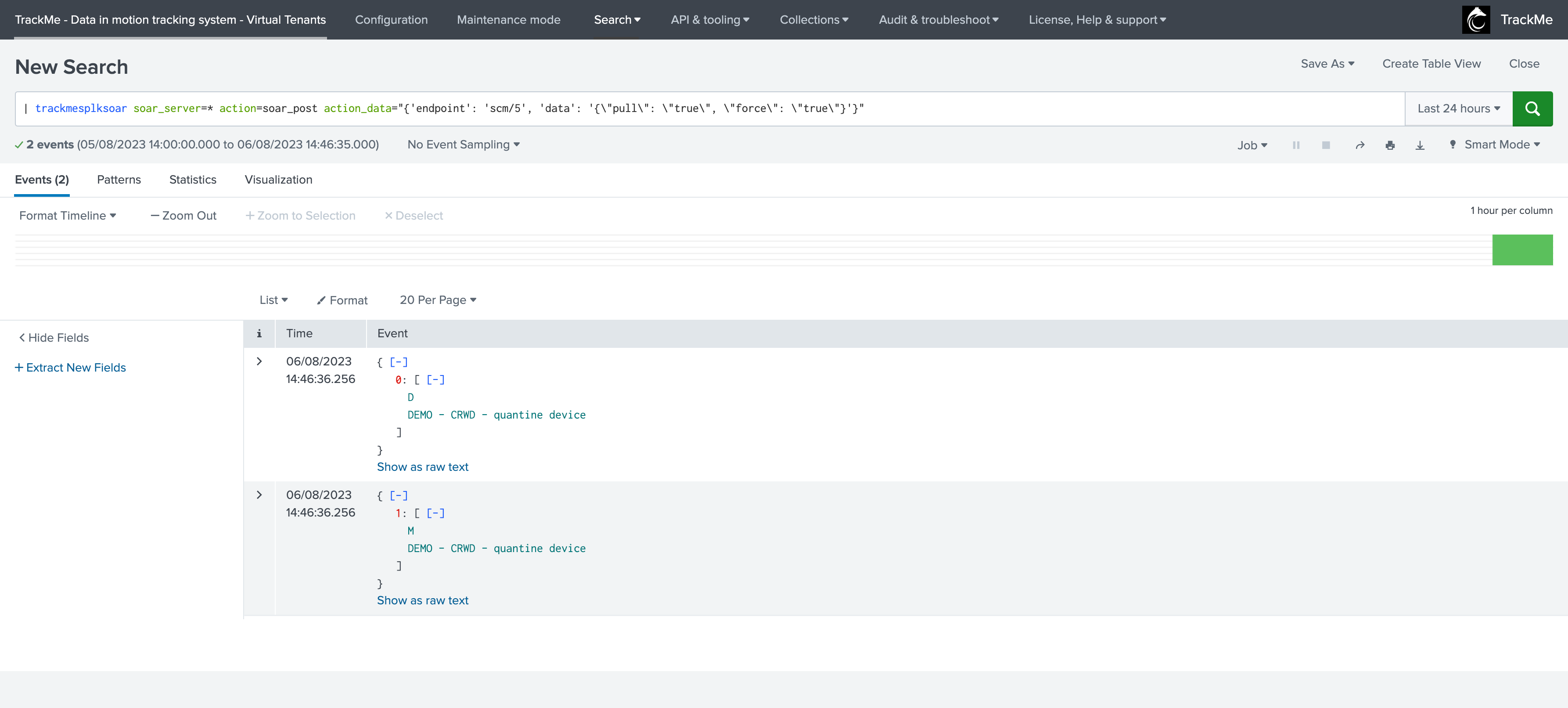
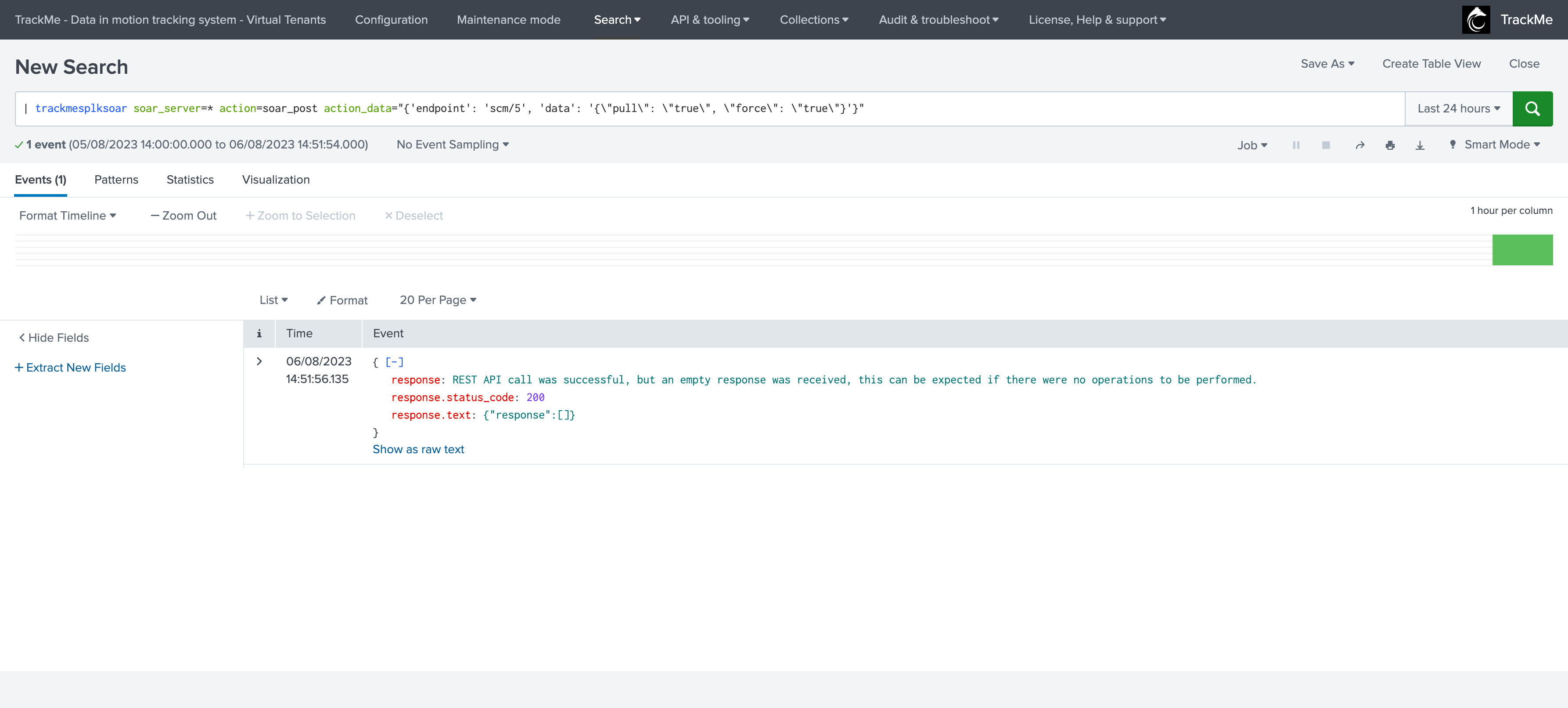
If we had no operations pending, we would have got the following message returned:
6.4 Performing live REST SOAR lookups in TrackMe using the command trackmesplksoarlookup
TrackMe provides a new command called trackmesplksoarlookup which allows to perform live REST lookups to the SOAR API, and to retrieve the metadata associated with the SOAR objects such as the playbooks, assets, applications and brokers associated with the detection.
Usage of the command:
[trackmesplksoarlookup-command]
syntax = | trackmesplksoarlookup soar_server=<soar_server> endpoint_target=<endpoint_target> source_field=<source_field> dest_field_name=<dest_field_name> dest_field_definition=<dest_field_definition> definition_filter_fields=<A comma separated list of fields to retrieve from the definition>
description = \
This streaming command can be used to interact with the SOAR API in a lookup way, so that from an id of an object, its definition can be retrieved easily in native SPL \
Syntax: \
- soar_server: the name of the SOAR server as configured in the Splunk App for SOAR, \
- endpoint_target: the endpoint target for the object to lookup\
- source_field: the name of the field containing the object id, \
- dest_field_name: the name of the field to store the logical name of the corresponding object retrieved from this id (if any!), \
- dest_field_definition: the name of the field to store the definition of the corresponding object retrieved from this id (if any!) \
- definition_filter_fields: a comma separated list of fields to retrieve from the definition \
| trackmesplksoarlookup soar_server=<soar_server> endpoint_target=<endpoint_target> source_field=<source_field> dest_field_name=<dest_field_name> dest_field_definition=<dest_field_definition> definition_filter_fields=<A comma separated list of fields to retrieve from the definition>
comment1 = \
Lookup the definition of a SOAR object from its id in a streaming manner
example1 = \
| makeresults | eval asset=1 | trackmesplksoarlookup soar_server=* endpoint_target=asset source_field=asset dest_field_name=asset_name dest_field_definition=asset_definition definition_filter_fields="name,description"
shortdesc = Streaming command for TrackMe's Splunk SOAR integration
Example:
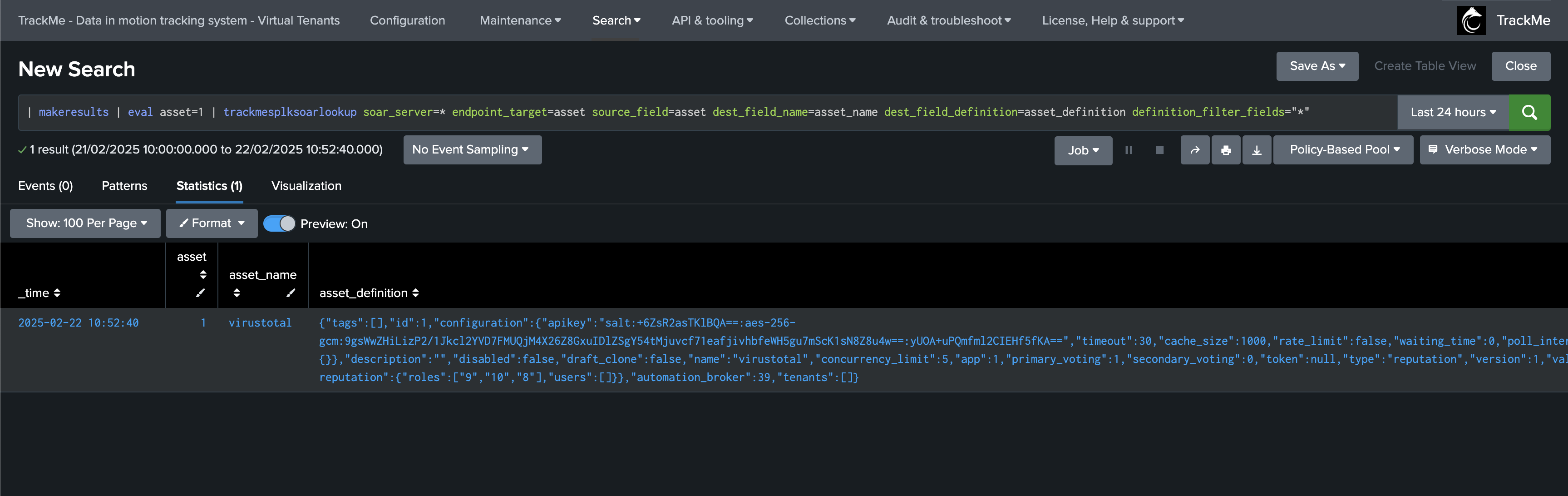
You can for instance use the lookup command to retrieve the definition any SOAR object in pure SPL:
| makeresults | eval asset=1 | trackmesplksoarlookup soar_server=* endpoint_target=asset source_field=asset dest_field_name=asset_name dest_field_definition=asset_definition definition_filter_fields="*"
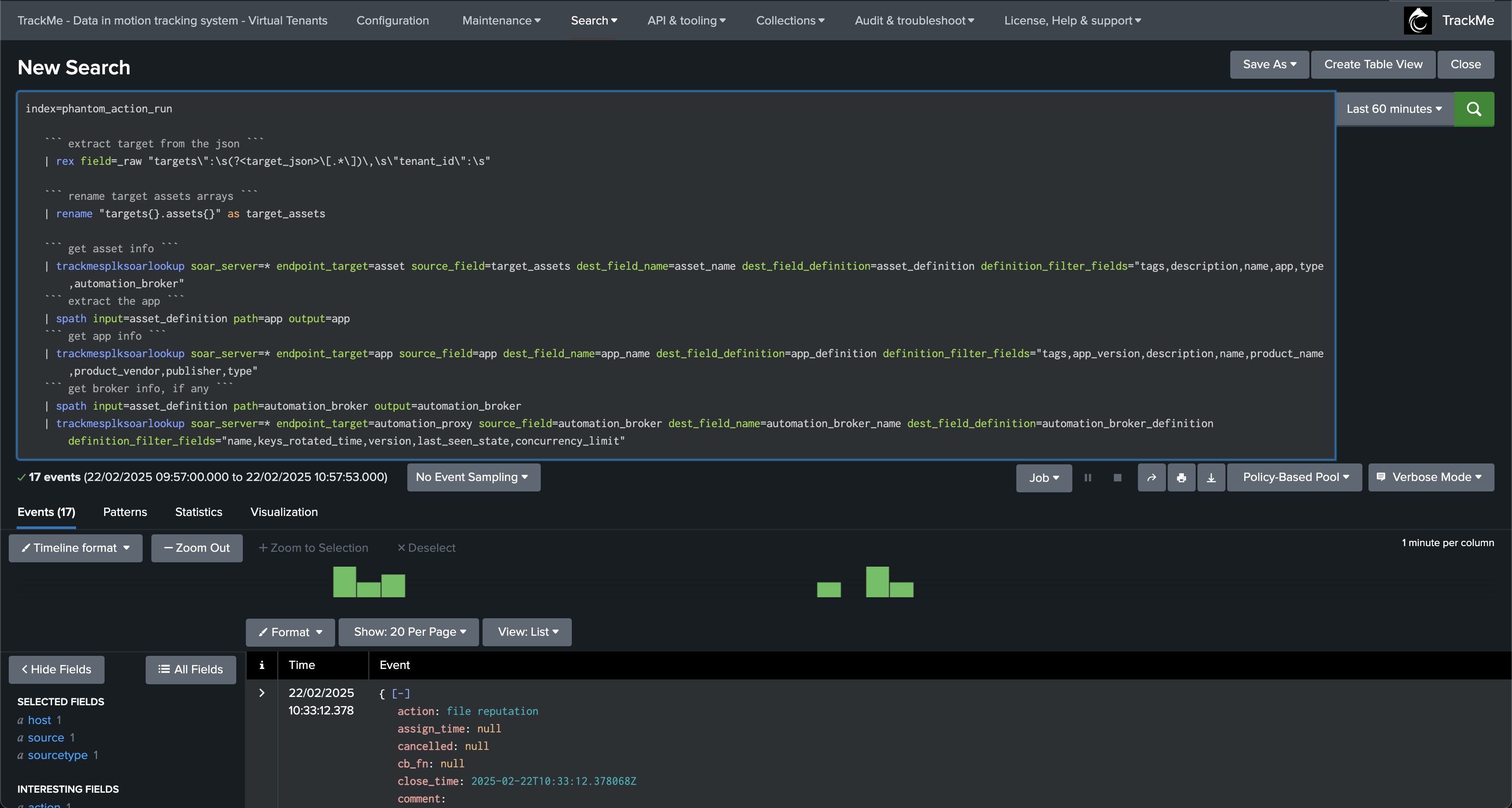
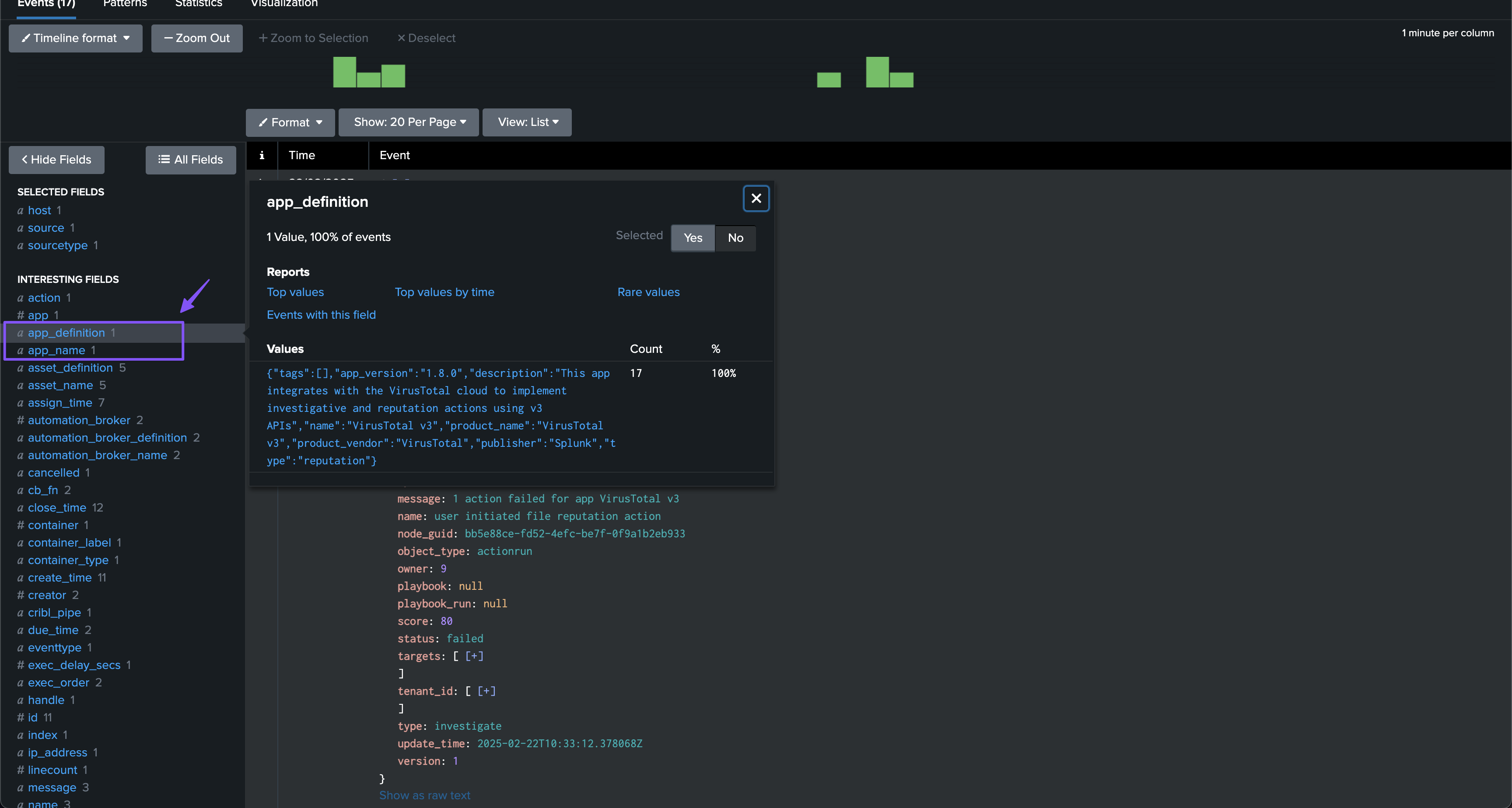
A full usage example can be to track SOAR actions and call the command to lookup associated objects metadata using their IDs:
index=phantom_action_run
``` extract target from the json ```
| rex field=_raw "targets\":\s(?<target_json>\[.*\])\,\s\"tenant_id\":\s"
``` rename target assets arrays ```
| rename "targets{}.assets{}" as target_assets
``` get playbook info ```
| trackmesplksoarlookup soar_server=* endpoint_target=playbook source_field=playbook dest_field_name=playbook_name dest_field_definition=playbook_definition definition_filter_fields="tags,active,category,comment,labels,name,metadata,playbook_type"
``` get asset info ```
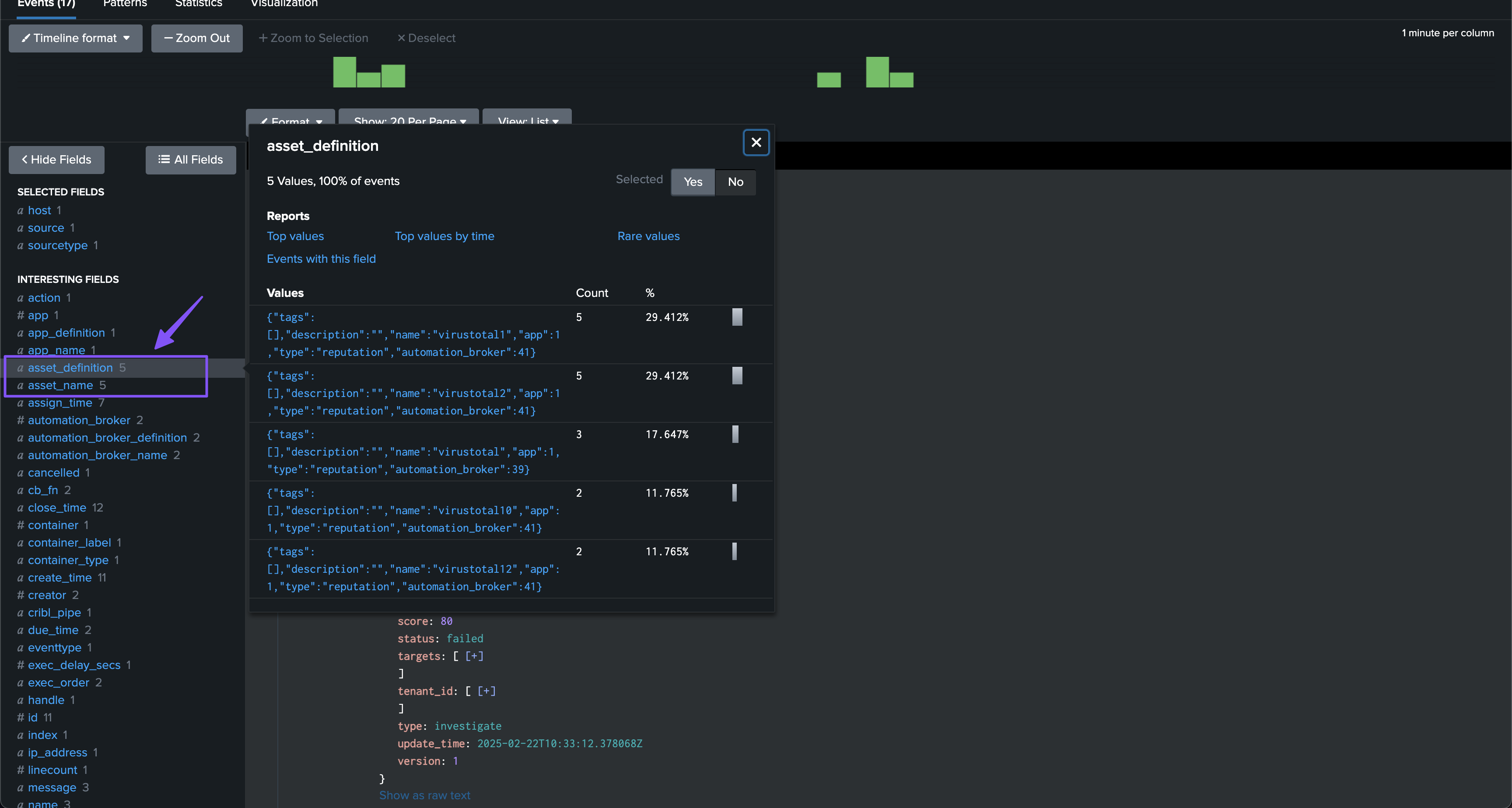
| trackmesplksoarlookup soar_server=* endpoint_target=asset source_field=target_assets dest_field_name=asset_name dest_field_definition=asset_definition definition_filter_fields="tags,description,name,app,type,automation_broker"
``` extract the app ```
| spath input=asset_definition path=app output=app
``` get app info ```
| trackmesplksoarlookup soar_server=* endpoint_target=app source_field=app dest_field_name=app_name dest_field_definition=app_definition definition_filter_fields="tags,app_version,description,name,product_name,product_vendor,publisher,type"
``` get broker info, if any ```
| spath input=asset_definition path=automation_broker output=automation_broker
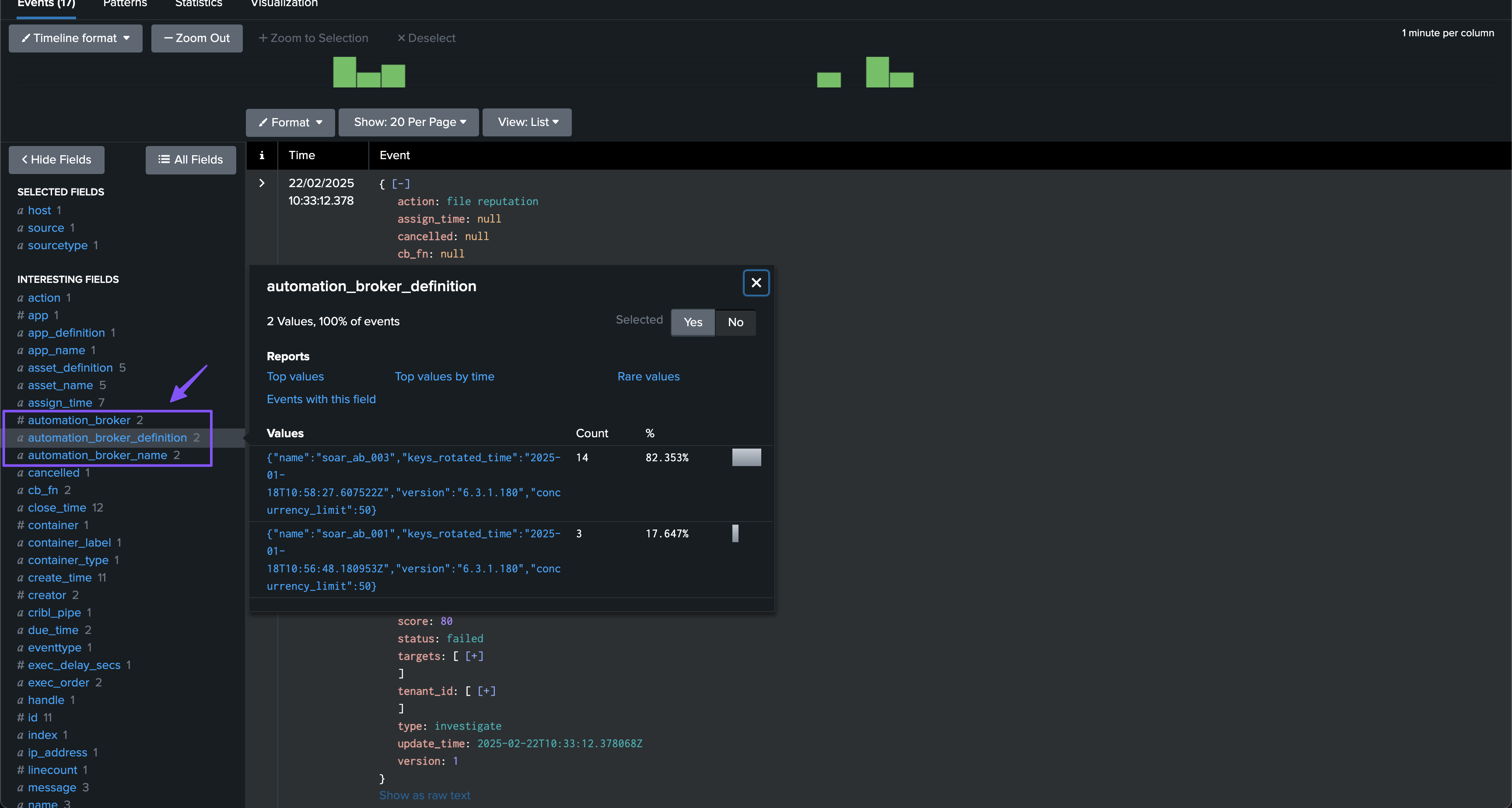
| trackmesplksoarlookup soar_server=* endpoint_target=automation_proxy source_field=automation_broker dest_field_name=automation_broker_name dest_field_definition=automation_broker_definition definition_filter_fields="name,keys_rotated_time,version,last_seen_state,concurrency_limit"
6.5 TrackMe’s REST API splk-soar endpoints
Underneath, the trackmesplksoar command interacts with the TrackMe API endpoints for SOAR, you can find the endpoints references and their documentation in the API reference dashboard: (Menu API & Tooling)