Splunk Remote Deployments (splunkremotesearch)
Overview of Splunk Remote Search Capabilities in TrackMe
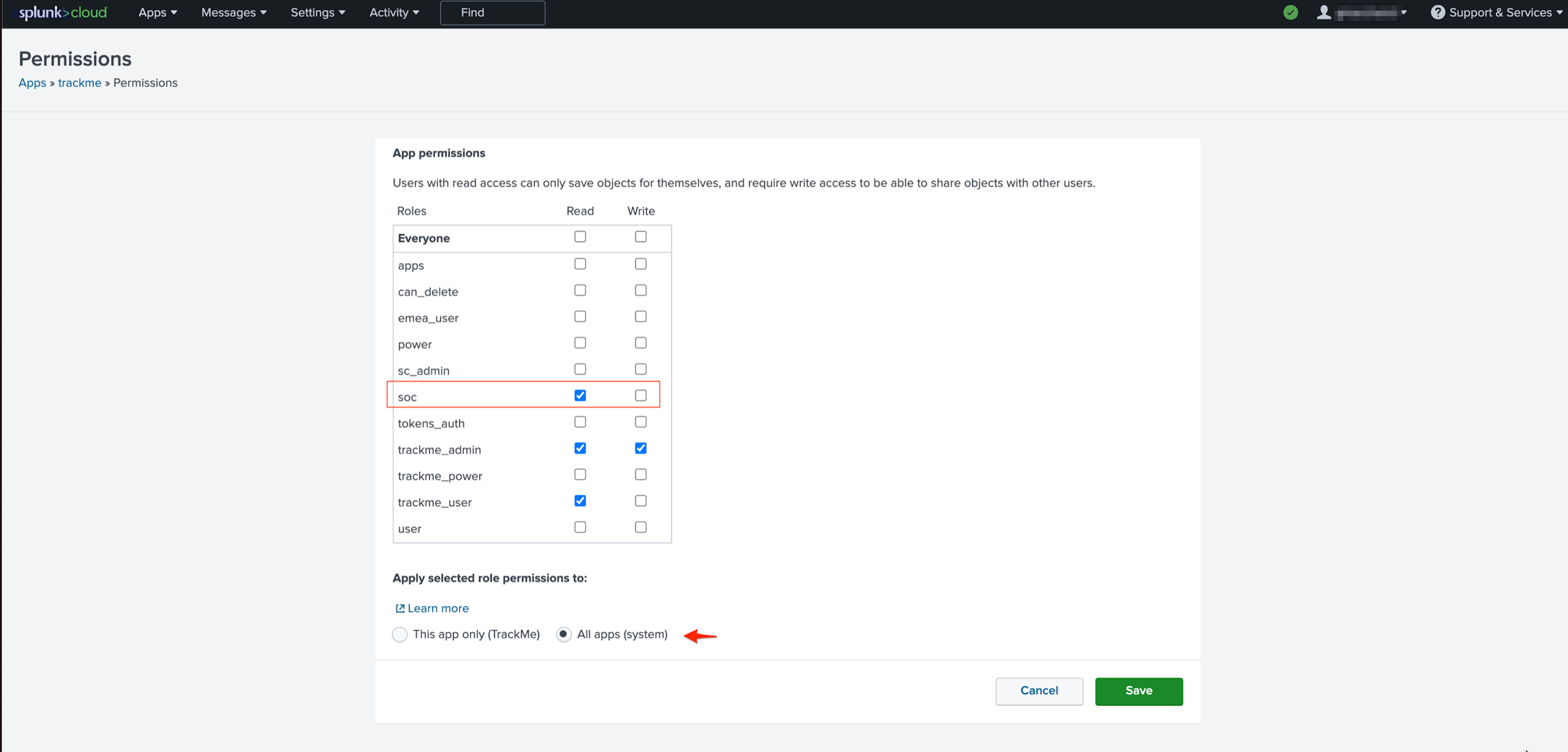
TrackMe can manage locally available data, as well as data from remote Splunk deployments (Splunk Enterprise, Splunk Cloud) and remote independent instances such as utility nodes (Deployment Servers, Cluster Managers, License Manager, etc.) or Heavy Forwarders.
This is a key capability provided by TrackMe, which is used transparently when you configure trackers, allowing you to target either the local environment where TrackMe is hosted, or any other Splunk remote deployment.
There are plenty of use cases where this capability of TrackMe is game-changing, enabling TrackMe to become the single pane of glass for your monitoring and operations.
The Splunk remote search feature in TrackMe relies on multiple aspects:
The
splunkremotesearchTrackMe generating custom command, which relies on the Splunk Python SDK to perform searches remotely at scaleThe concept of accounts which allows TrackMe to store and access pre-configured configuration defining the Splunk remote environment
Various backend-level features in TrackMe designed to identify and handle the remote entities accordingly
The Remote deployment concept can be used for various purposes, from feeds tracking on remote deployments, to Flex objects, CIM compliance tracking, or Workload between different Search Head tiers
Note
Local service account user or SAML service account
On the remote Search Heads tier counterpart, you can use a local user or a SAML user associated with the bearer token
However, to use SAML, your SAML setup needs to support AQR and it needs to be configured
Reference: https://docs.splunk.com/Documentation/Splunk/latest/Security/Setupauthenticationwithtokens
Reference: https://docs.splunk.com/Documentation/SplunkCloud/latest/Security/SAMLConfigJWT
Hint
TrackMe supports multiple REST endpoints per account, with High Availability and Disaster Recovery capabilities: (from version 2.0.22)
For each account, you can specify a comma-separated list of REST endpoints per account
TrackMe will automatically verify the connectivity and randomly choose a REST endpoint target among any reachable endpoints
Therefore, you can specify multiple endpoints to support high availability and distribution of the searches against multiple endpoints automatically
This capability can be useful, for example, if you deal with a Search Head Cluster and cannot use a load balancer or VIP to access the cluster
Hint
TrackMe supports and requires Role-Based Access Control per Remote account defined: (from version 2.0.34)
For each account, you need to specify a comma-separated list of Splunk roles that are allowed to use this Remote account
For retro-compatibility purposes, if the roles for an existing account have not been set up yet, TrackMe will use built-in roles in addition to typical admin roles (admin, sc_admin, trackme_user, trackme_power, trackme_admin)
If the user calling the
splunkremotesearchcommand is not a member of the account-specified roles, access will be refusedFrom version 2.0.61, both direct membership and inheritance are supported; users need to be a member of any of the provided roles, or a role which inherits from any of these roles
Hint
TrackMe automatically performs the rotation of Bearer tokens: (from version 2.1.8)
Since TrackMe 2.1.8, we support automated rotation of the Splunk bearer tokens for remote accounts
For every Splunk remote account, TrackMe will automatically try to rotate the bearer token based on the remote account’s configured retention (every 7 days by default)
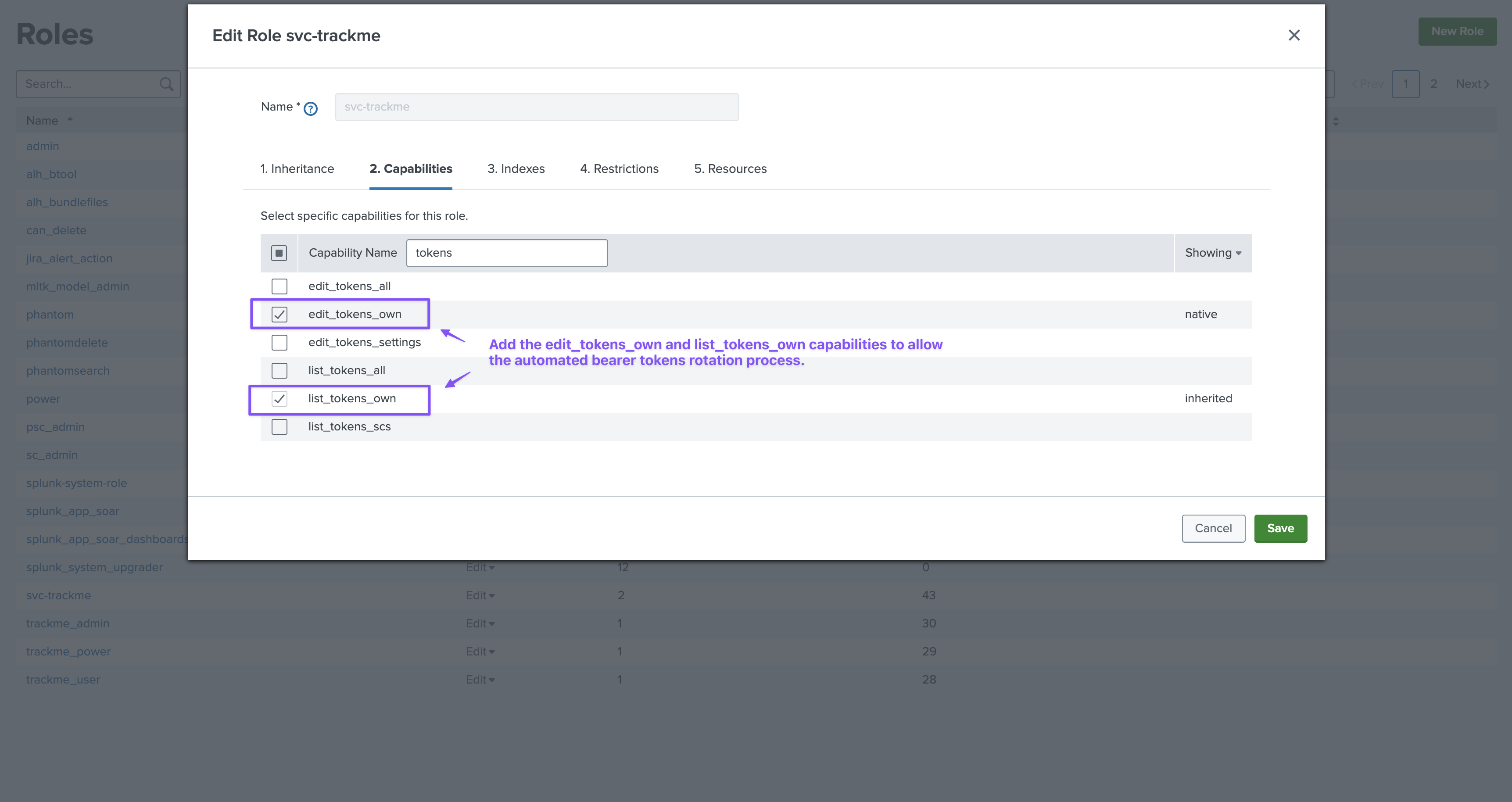
This requires the Splunk service account on the remote side to own the capabilities
list_tokens_allandedit_tokens_own, so the token can be created and the previous token revokedThe token renewal and revocation process is orchestrated by the general health tracker, which is executed once per day
Note that the initial token you have manually created will not be revoked by TrackMe, and would be disabled automatically depending on your settings
Hint
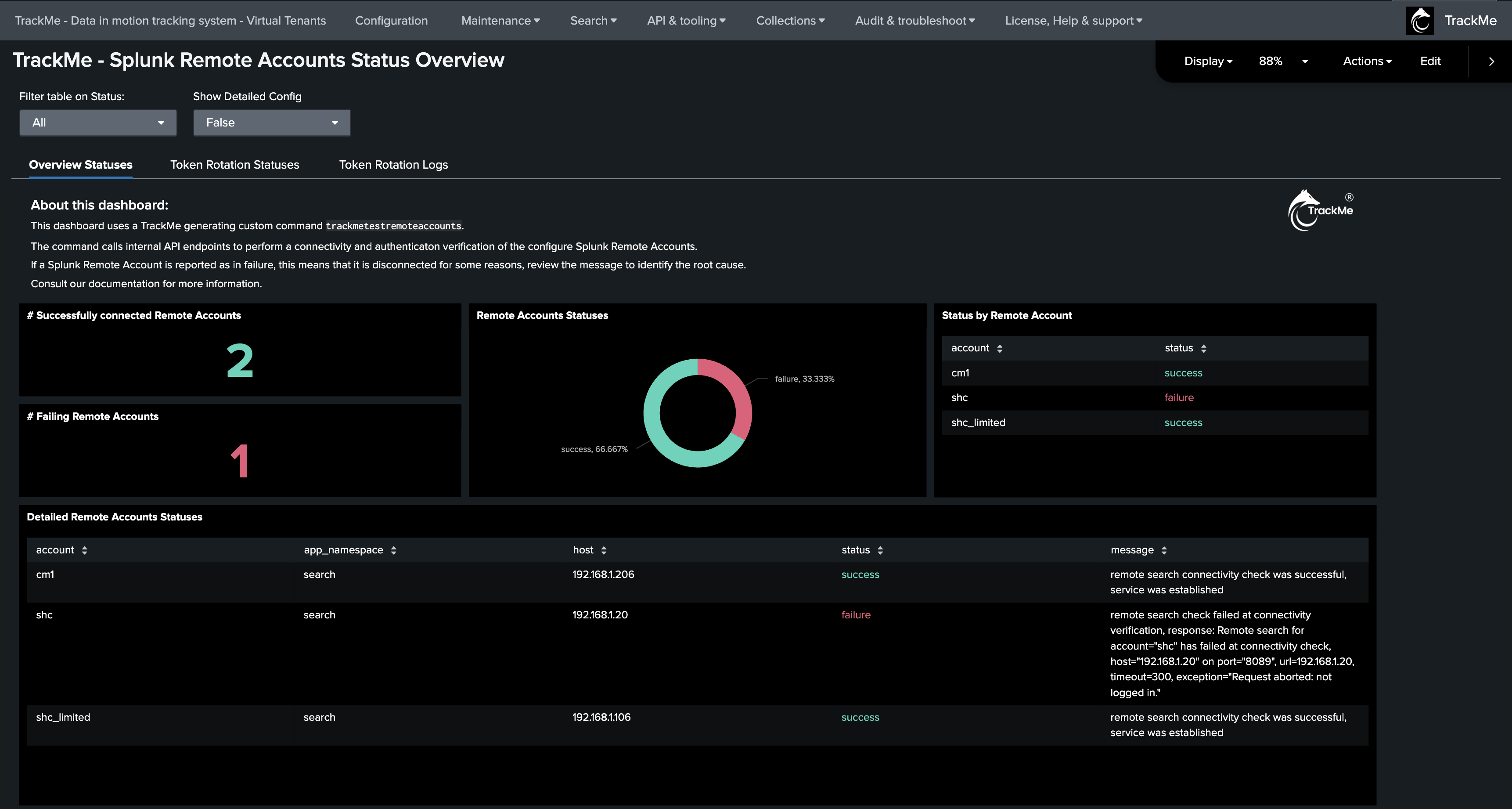
TrackMe Audit dashboard: Splunk Remote Account Overview (from version 2.1.16)
TrackMe now includes an Audit dashboard to monitor the Splunk remote accounts
This dashboard is available from the menu
Audit & Troubleshooting->Audit - Splunk Remote Accounts OverviewThis dashboard provides a comprehensive overview of the Splunk remote accounts, including the bearer token rotation process
Minimal RBAC Requirements for the Remote User Account
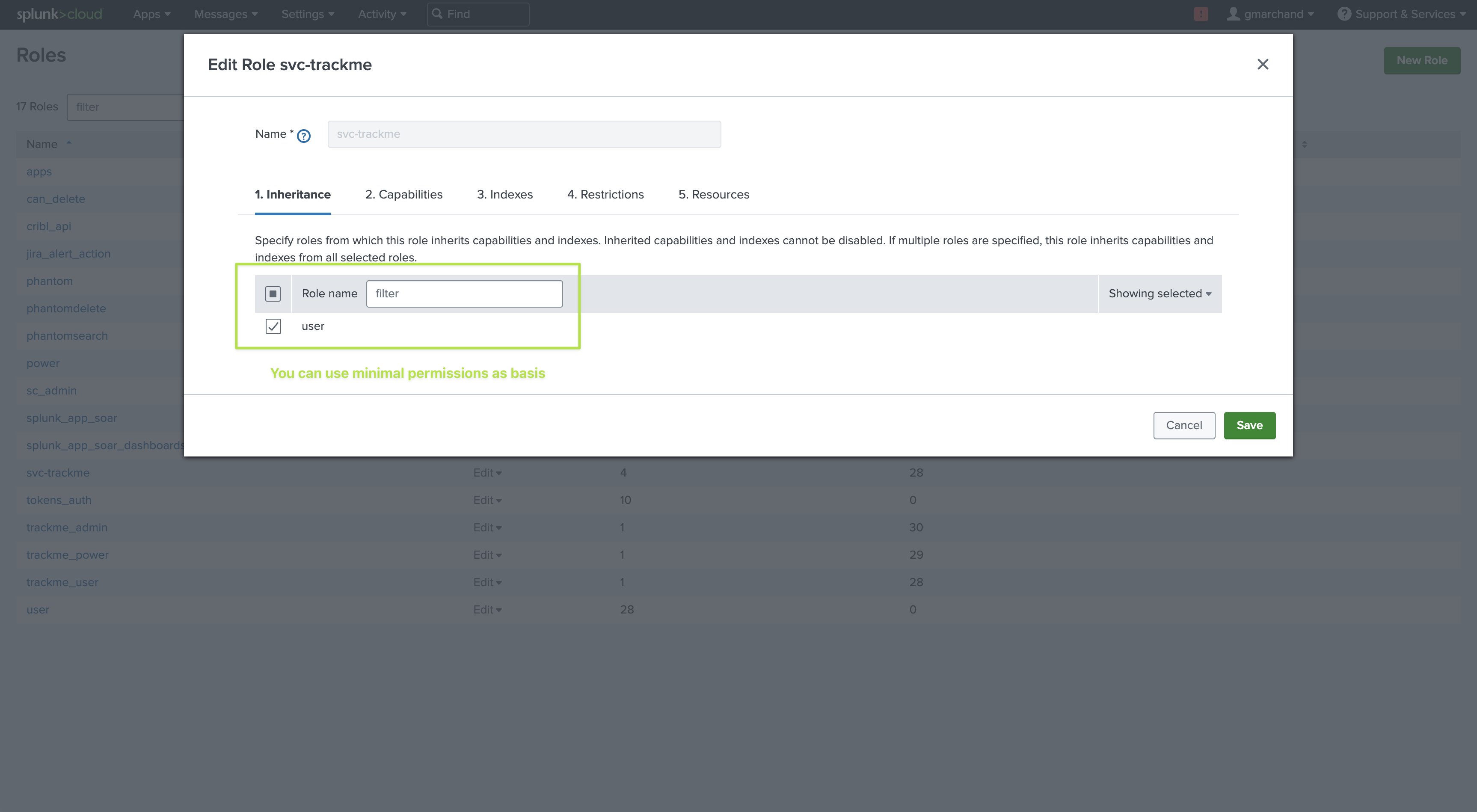
TrackMe remote capabilities rely on a Splunk bearer token authentication; this token is associated with a Splunk user on the remote side which itself is associated with specific roles, capabilities, permissions, and resource restrictions:
Roles and capabilities: The user can be created with minimal permissions using the Splunk
userrole out of the box (You can inherit from user or a role providing the same capabilities as power)Additional capabilities for tokens rotation: To allow the automated bearer tokens rotation, the user needs to have the capability
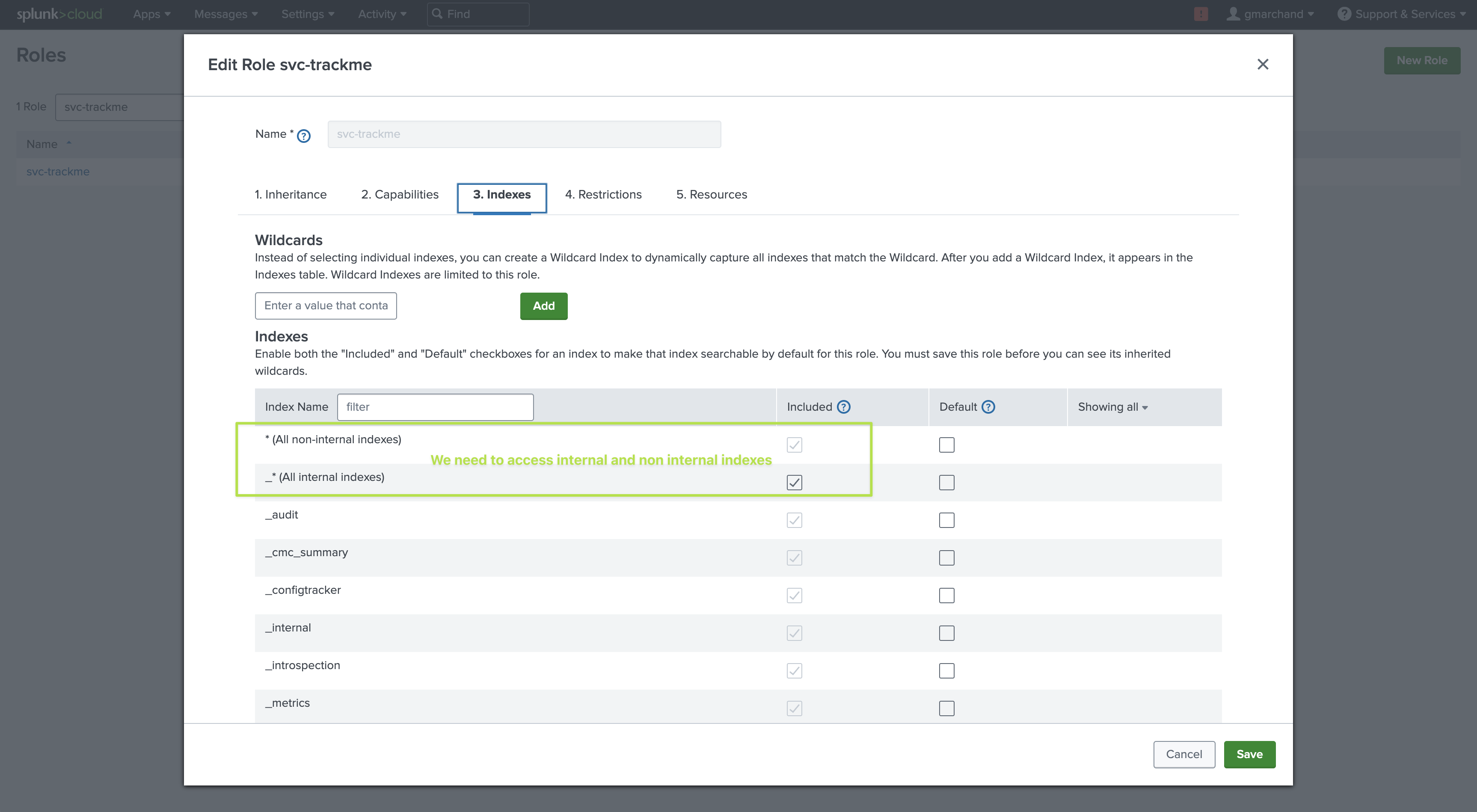
list_tokens_ownandedit_tokens_ownIndexes: Make sure the user can access both normal and
internalindexesRestrictions: The user for TrackMe should not have any time limits restrictions, as there are use cases which require long-term searches
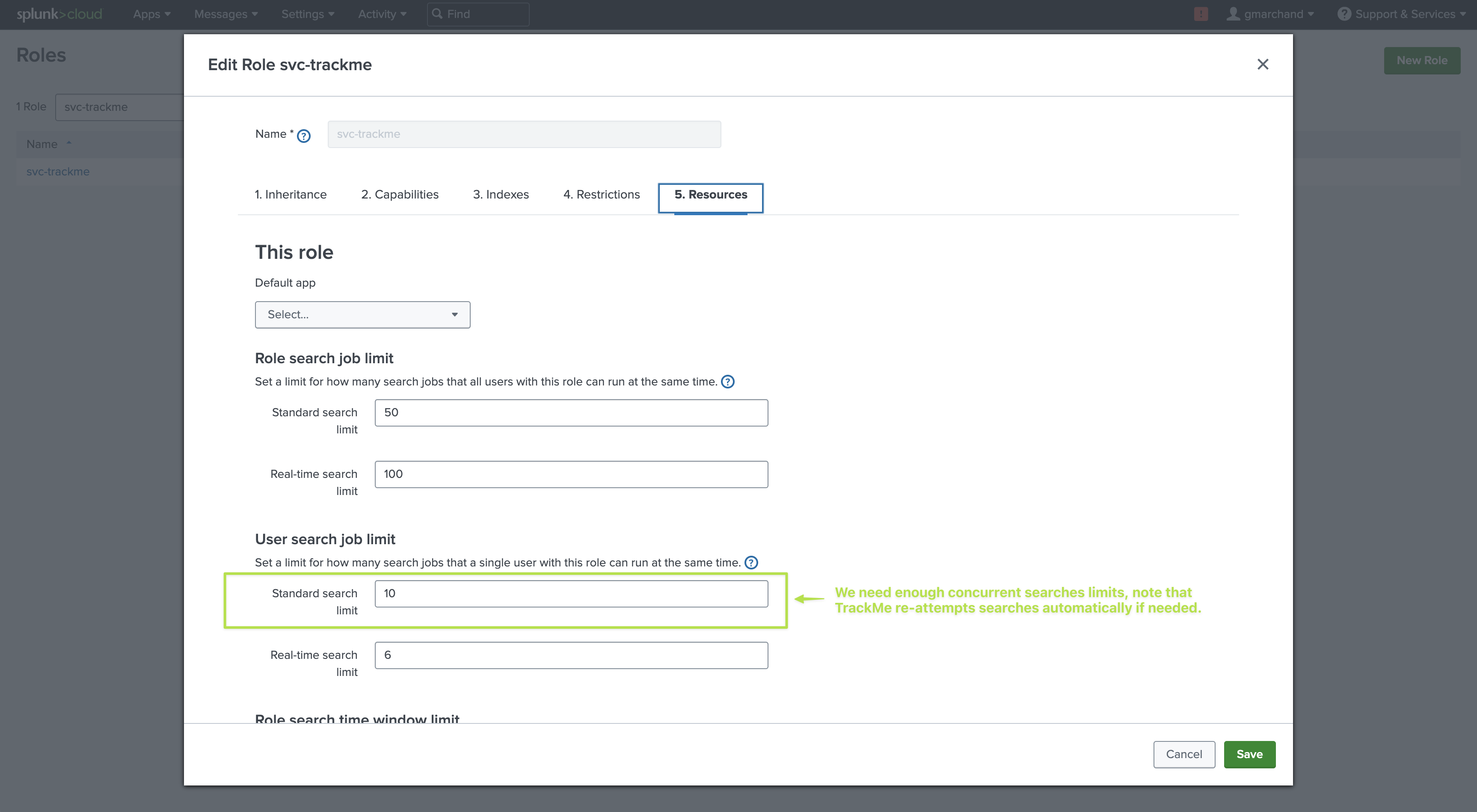
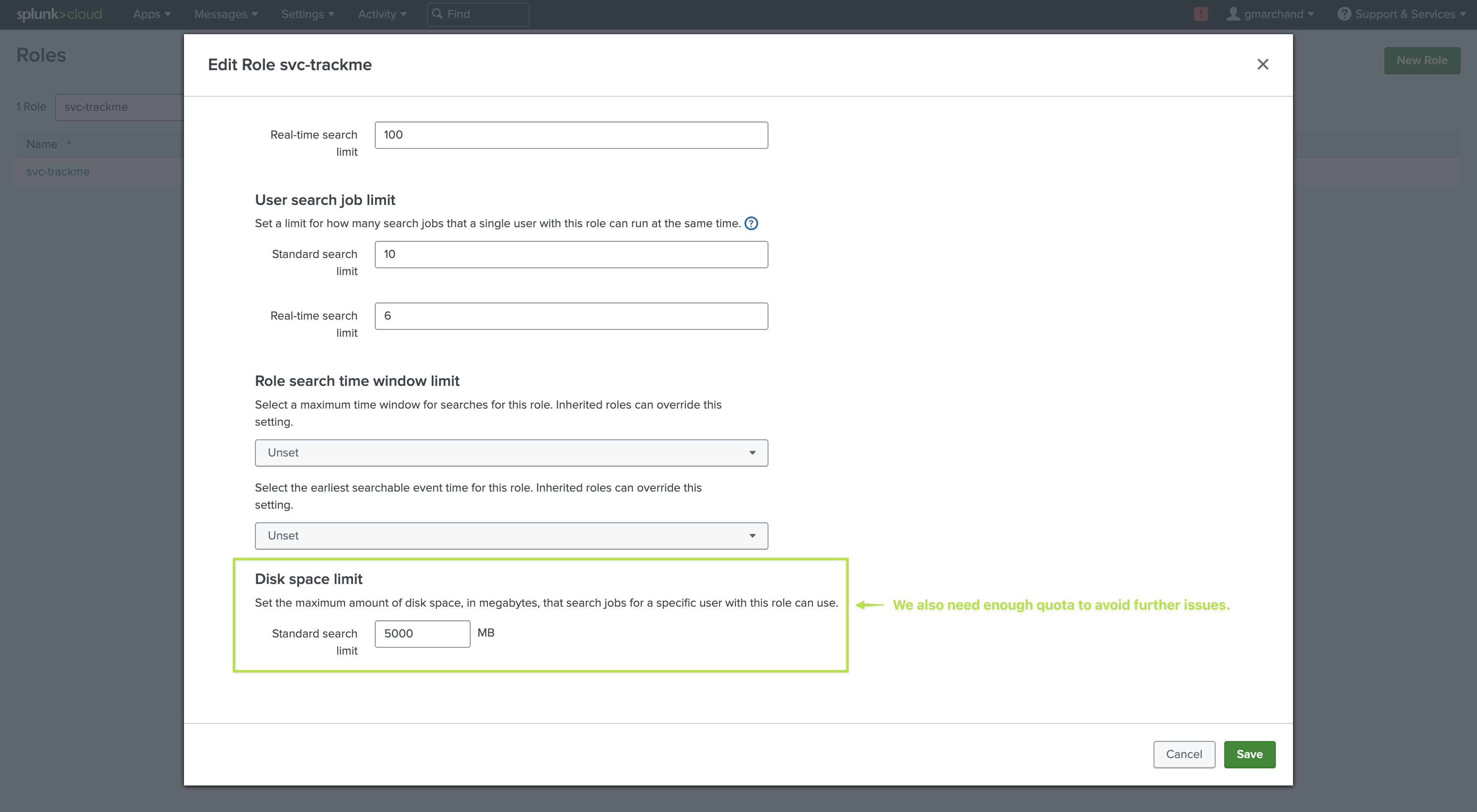
Resources: It is recommended to give this user enough concurrent searches (unlike a very basic or minimal user) as well as a sufficient quota (5GB or 10GB for instance)
Configuring a New Remote Account
When configuring a Splunk Remote deployment, you will provide:
A name which uniquely identifies the account (the account ID)
The URL of the Splunk Search Head REST API, this can be a Fully Qualified Domain Name, a hostname, or an IP address (which itself can be a load balancer)
Multiple REST endpoints can be submitted as a comma-separated list of targets
The bearer token value, which is the secured credential to access the environment, is securely stored in the Splunk credential store
The application namespace where remote searches are to be executed, defaults to the Search application on the remote target
A comma-separated list of Splunk roles allowed to use this account (membership or inheritance)
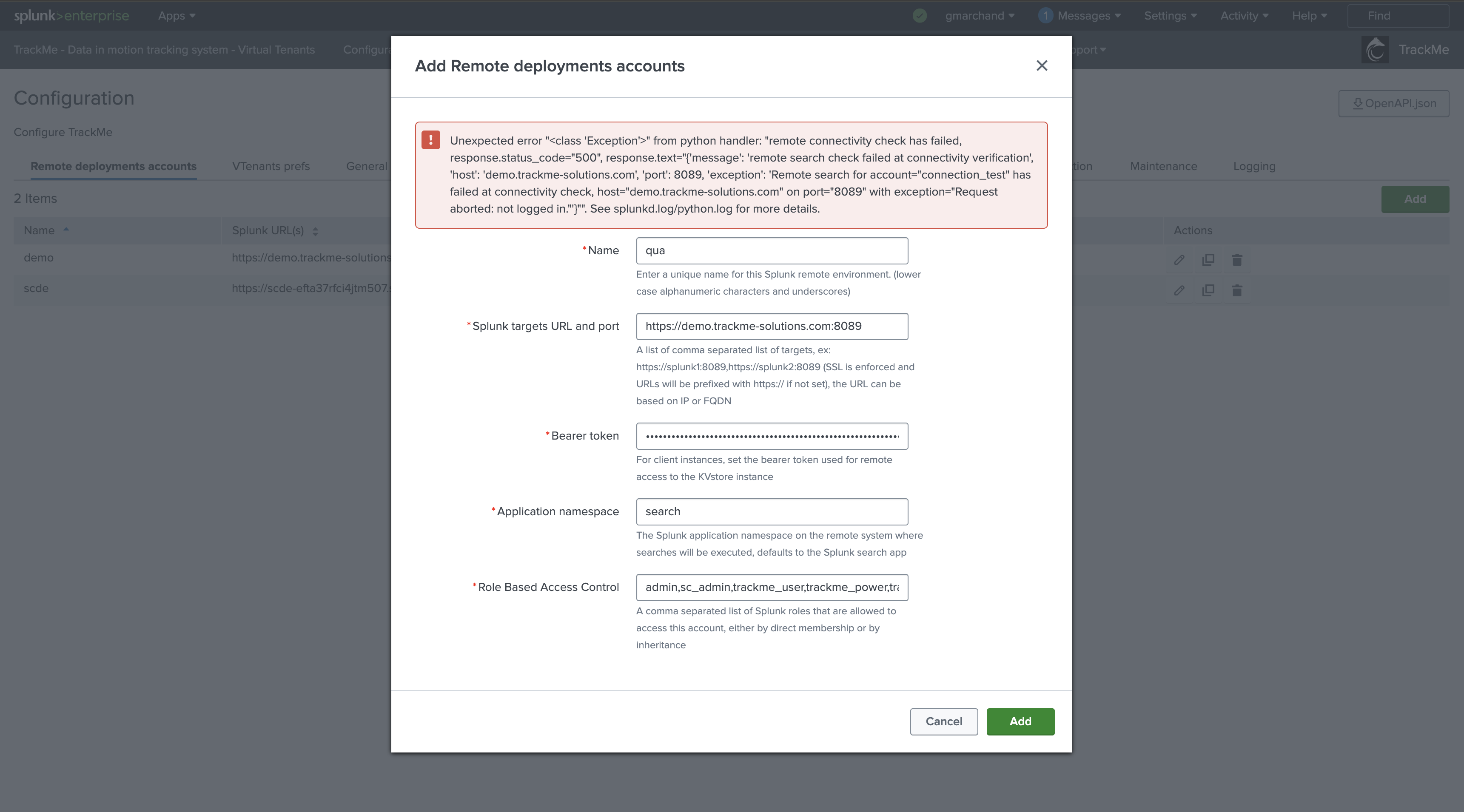
At the time of creation or later on if you edit the account, a connectivity check is automatically performed which validates the network connectivity and authentication. If the check fails, the interface will refuse the requested action
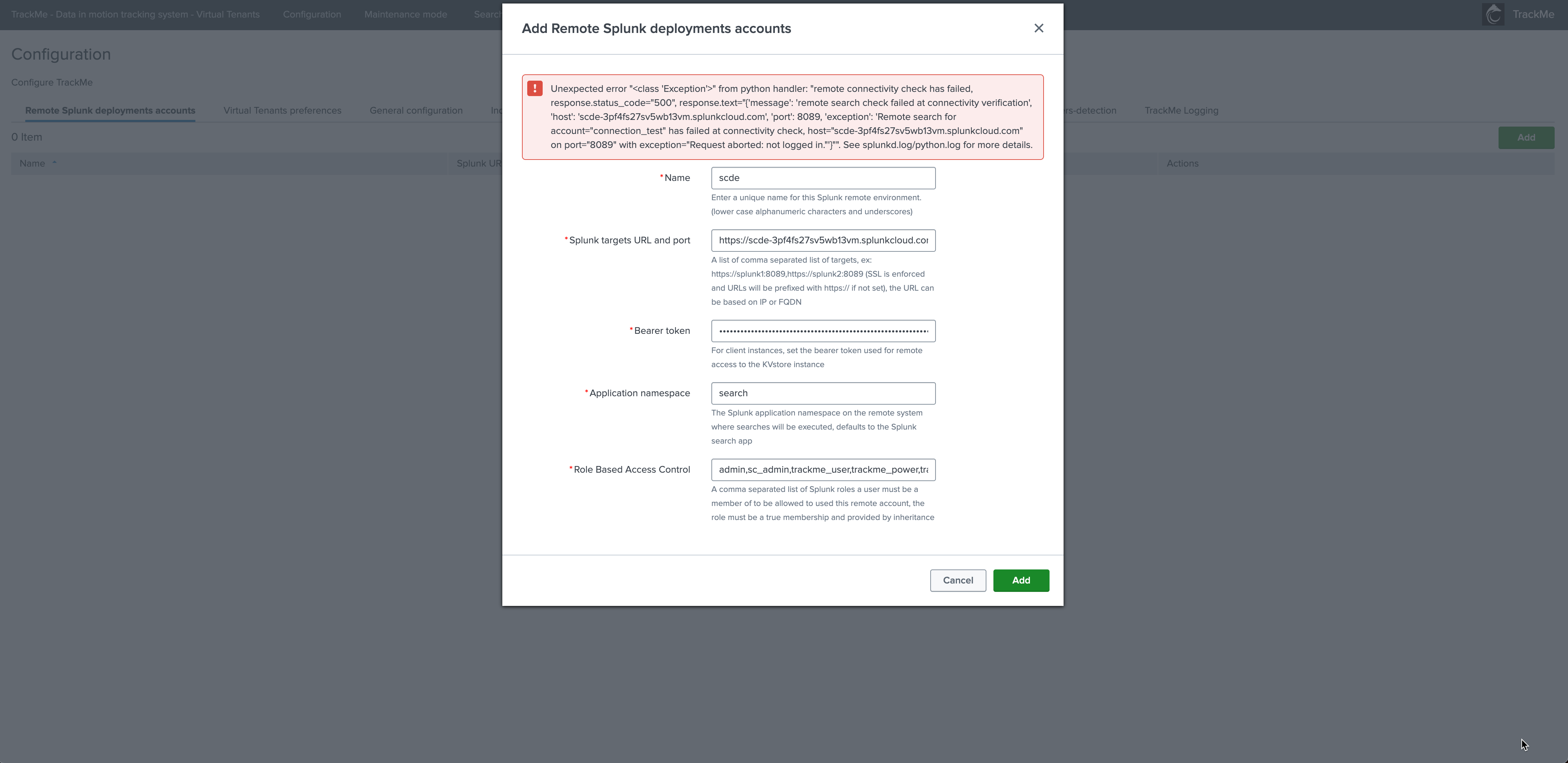
To configure a new remote account, access the Configuration user interface from the navigation bar:
If the connectivity check fails at the creation step, the configuration UI will raise an exception which indicates the root cause of the failure:
Once the account exists, you can test the connectivity easily using the following TrackMe REST endpoint in SPL:
| trackme mode=post url="/services/trackme/v2/configuration/test_remote_account" body="{'account': '<name of the account>'}"
The endpoint verifies that TrackMe can connect and authenticate successfully to the Splunk remote deployment.
When creating a new Virtual Tenant or a new Hybrid object, TrackMe will perform the same connectivity verification automatically:
Example of a Splunk Remote Search Performed by TrackMe
When performing Remote Splunk searches, TrackMe automatically defines an optimized search to split the search logic between the part executed remotely, and the search logic handled locally.
Example:
Using splunkremotesearch in a Different Application Namespace
To use the command splunkremotesearch from a different application than TrackMe, such as Search & Reporting, you need to perform a few steps as follows.
Manage Capabilities
TrackMe requires capabilities to be able to access the command splunkremotesearch; the user roles need to have the capability:
trackmeuseroperations
You can choose to inherit from the trackme_user role, or you can add the capability to your user roles as needed.
Note: Access is granted by any of the 3 built-in trackme_ user roles*
See: Role Based Access Control and ownership for more information about capabilities in TrackMe.
Manage Role-Based Access Control on the Account
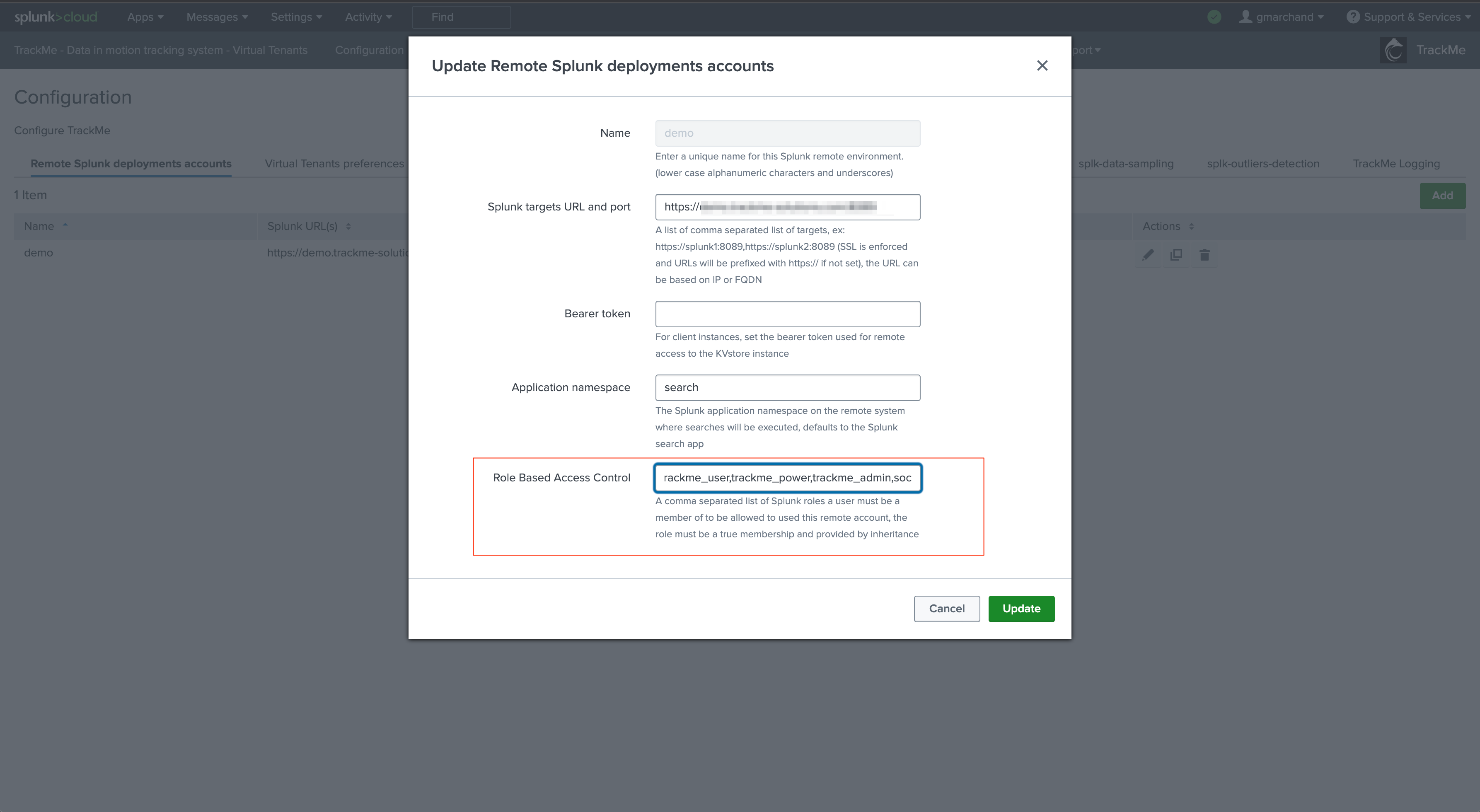
User roles need to be listed in the account; by default when creating an account, the following roles are listed:
admin, sc_admin, trackme_user, trackme_power, trackme_admin
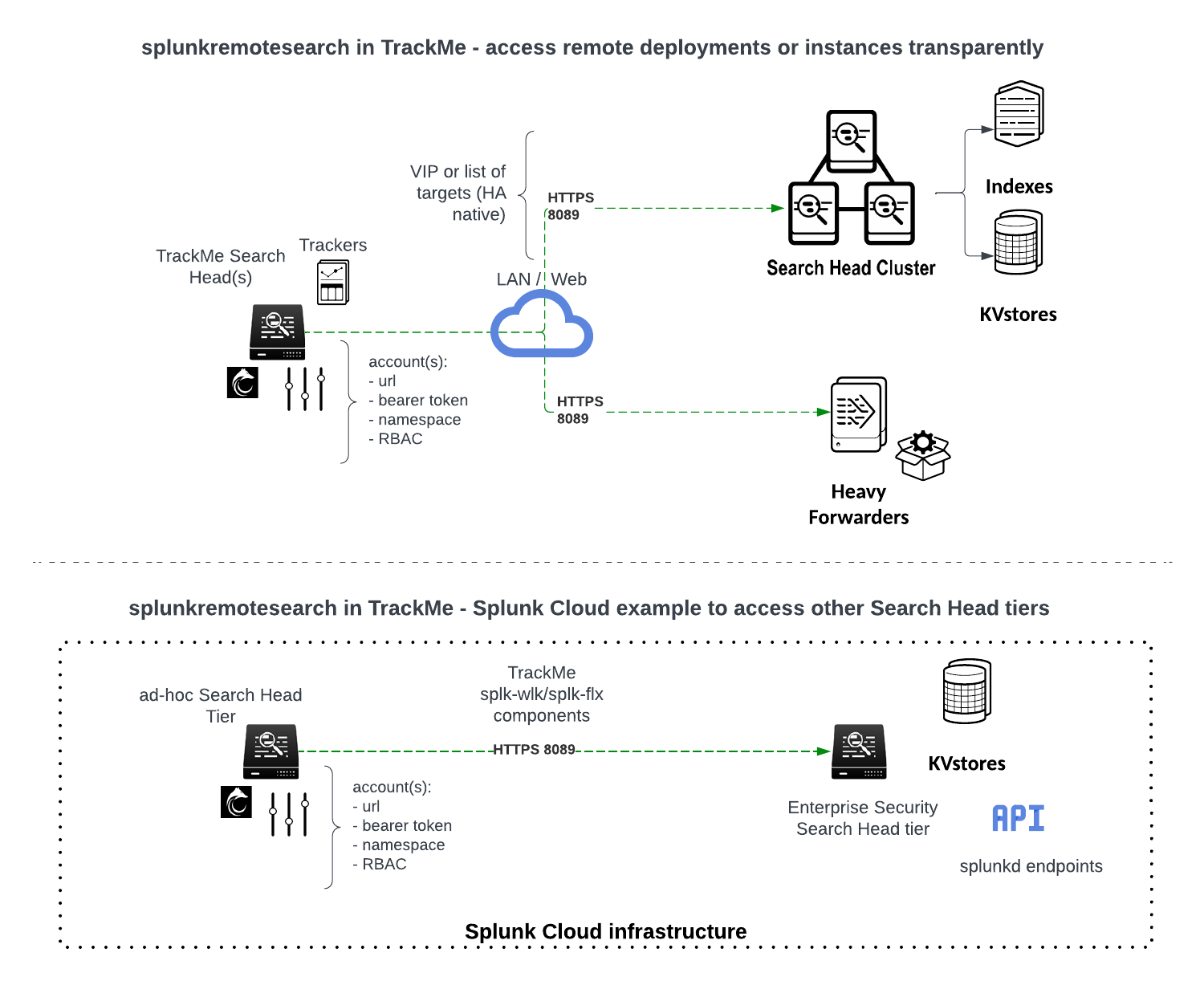
This is an explicit membership requirement; in our example, we grant the user role “soc” to allow a member of this role to use the splunkremotesearch command against this account:
Use the Command
In our example, the “soc” user is a member of a role with the same name, and can now use the splunkremotesearch command as needed to perform searches against the remote deployment, from any other application namespace:
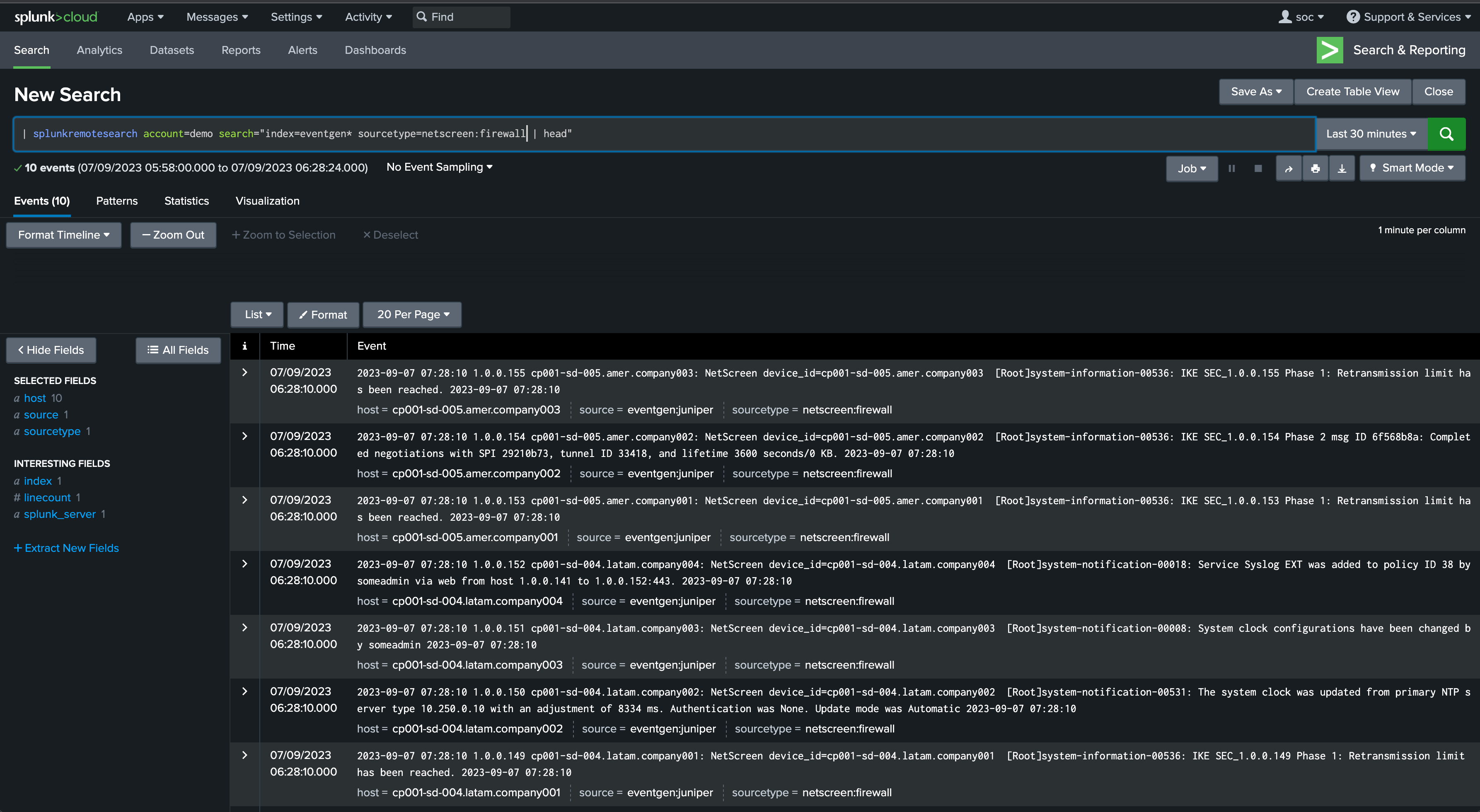
Accesses on the remote deployment rely on the service account which is associated with the bearer token configured in the account in TrackMe.
Troubleshooting Failure to Create or Update a Remote Account
TrackMe Remote Search capabilities are an API-based integration with Splunk API relying on Bearer token authentication; you can refer to:
When attempting to configure a new remote account, or update an existing account, TrackMe will attempt to validate the connectivity, both from a network and authentication perspective.
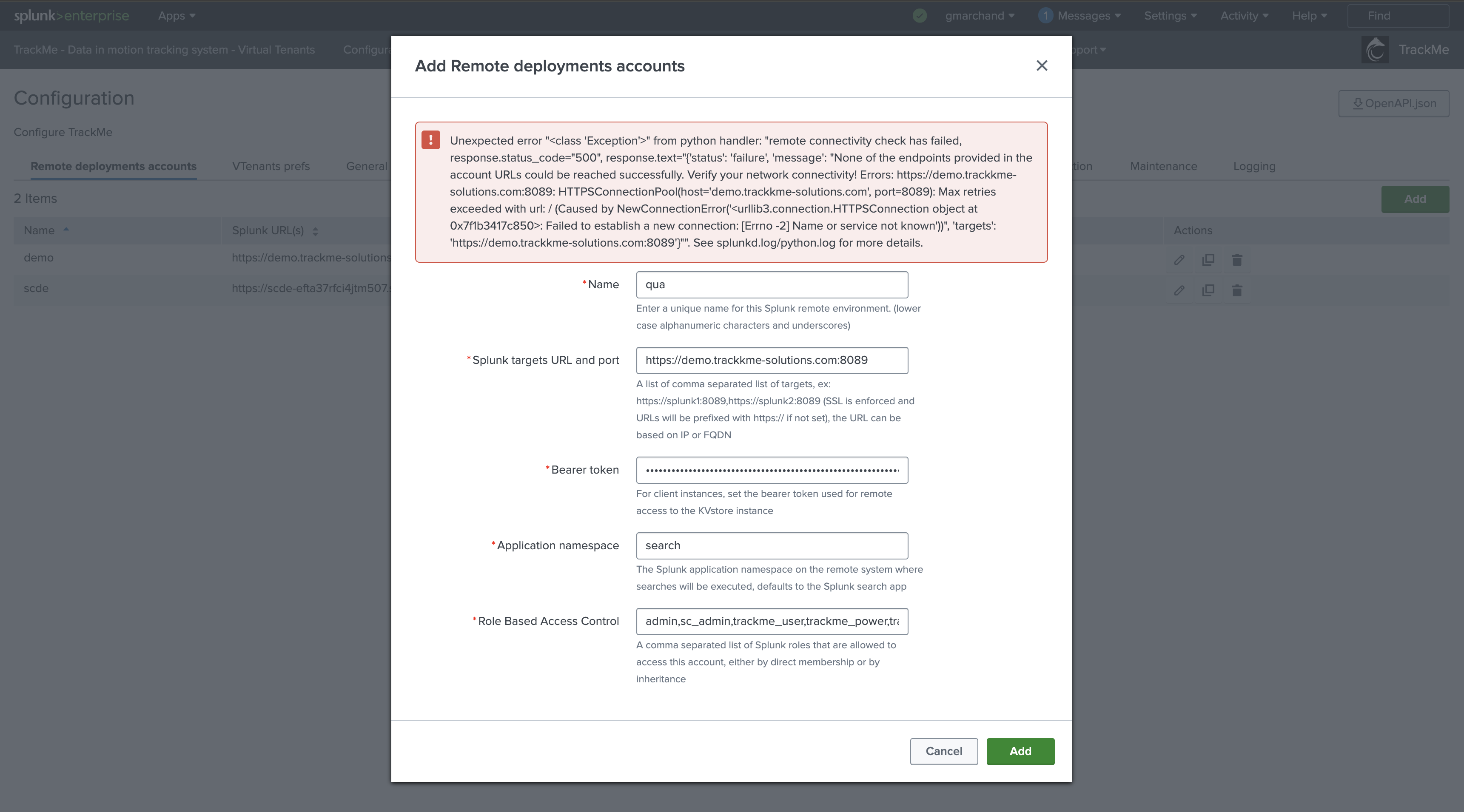
If this step fails, the UI will clearly raise and show the exception encountered, for instance:
Example of a network connectivity failure: (wrong host)
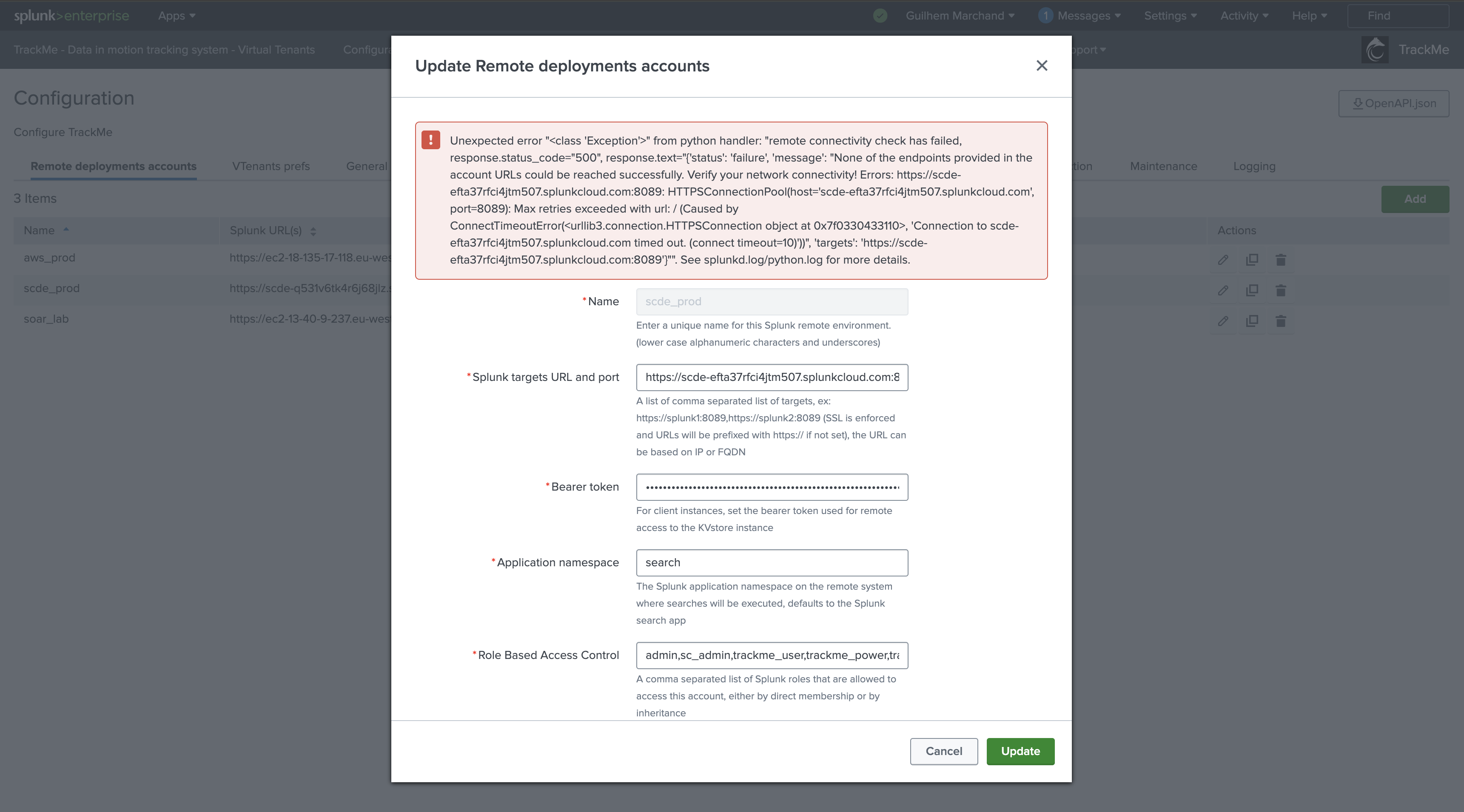
Example of a network connectivity failure: (timeout)
Example of a refused authentication by the remote counterpart:
Note: You can also test the connectivity in pure SPL via the following TrackMe REST API endpoint:
| trackme mode=post url="/services/trackme/v2/configuration/test_remote_connectivity" body="{'target_endpoints': 'https://mysplunk.mydomain.com:8089', 'bearer_token': 'xxxx', 'app_namespace': 'search'}"
Inspect splunkd.log logs on the remote counterpart:
If the connectivity fails for authentication related reasons, such as a wrong token or lack of capabilities, verify the splunkd.log on the remote counterpart, you can use the following Splunk search:
index=_internal source=*/splunkd.log JsonWebToken
Messages will be logged by Splunk, eventually indicating the root cause of the failure.
Example of a refused token:
02-05-2024 17:30:44.226 +0000 ERROR JsonWebToken [2843158 TcpChannelThread] - JsonWebToken validation failed because: Token xxxx-xxxx has an invalid signature.
Bearer tokens automated rotation and revoking
Since TrackMe 2.1.8, we support automated rotation of the Splunk bearer tokens for remote accounts, the process works as follows:
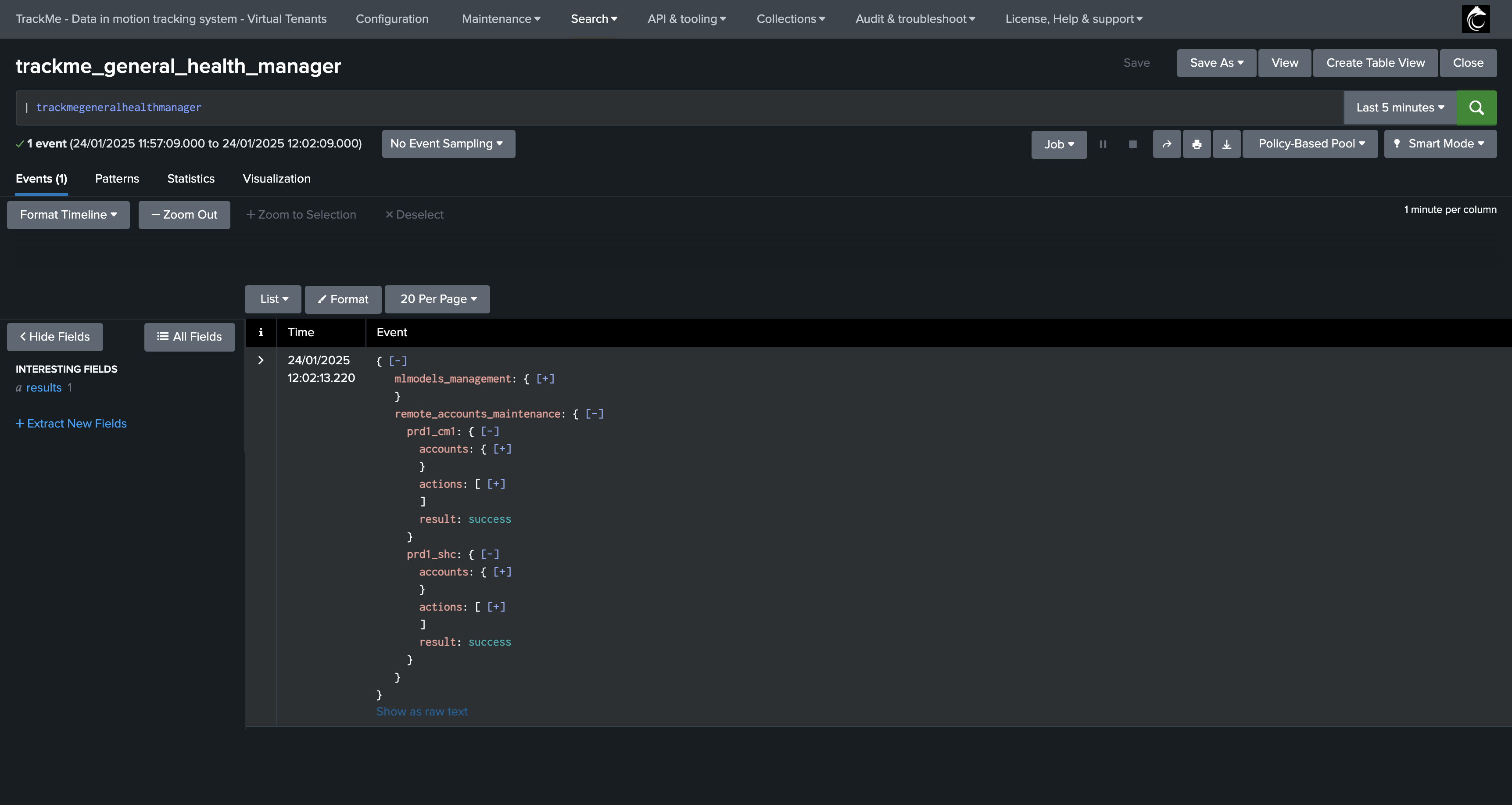
Once per day, a scheduled job called
trackme_general_health_manager(General Health Manager tracker) is executed.- This job calls the endpoint
/services/trackme/v2/configuration/admin/maintain_remote_accountfor each existing remote account, which does the following actions: Verify that the Remote account is up to date regarding available options, and update if necessary.
Verify if the Remote account has metadata available, and create/update if necessary. (stored in the KVstore
trackme_remote_account_token_expiration)If the Remote account bearer token has reached the rotation frequency, attempt to create a new bearer token, update the account and counters and finally revoke the previously generated token.
- This job calls the endpoint
Notes about the initial token and rotation process:
The initial token you have manually created will NOT be revoked by TrackMe, and would be disabled automatically depending on your settings.
Once at least one rotation has been performed, and if it was successful, the initial token is not used anymore.
From the stage of the first rotation, the previously generated and used token is automatically deleted by TrackMe, and the new token is automatically configured in the Splunk remote account.
Where to find bearer tokens rotation metadata?
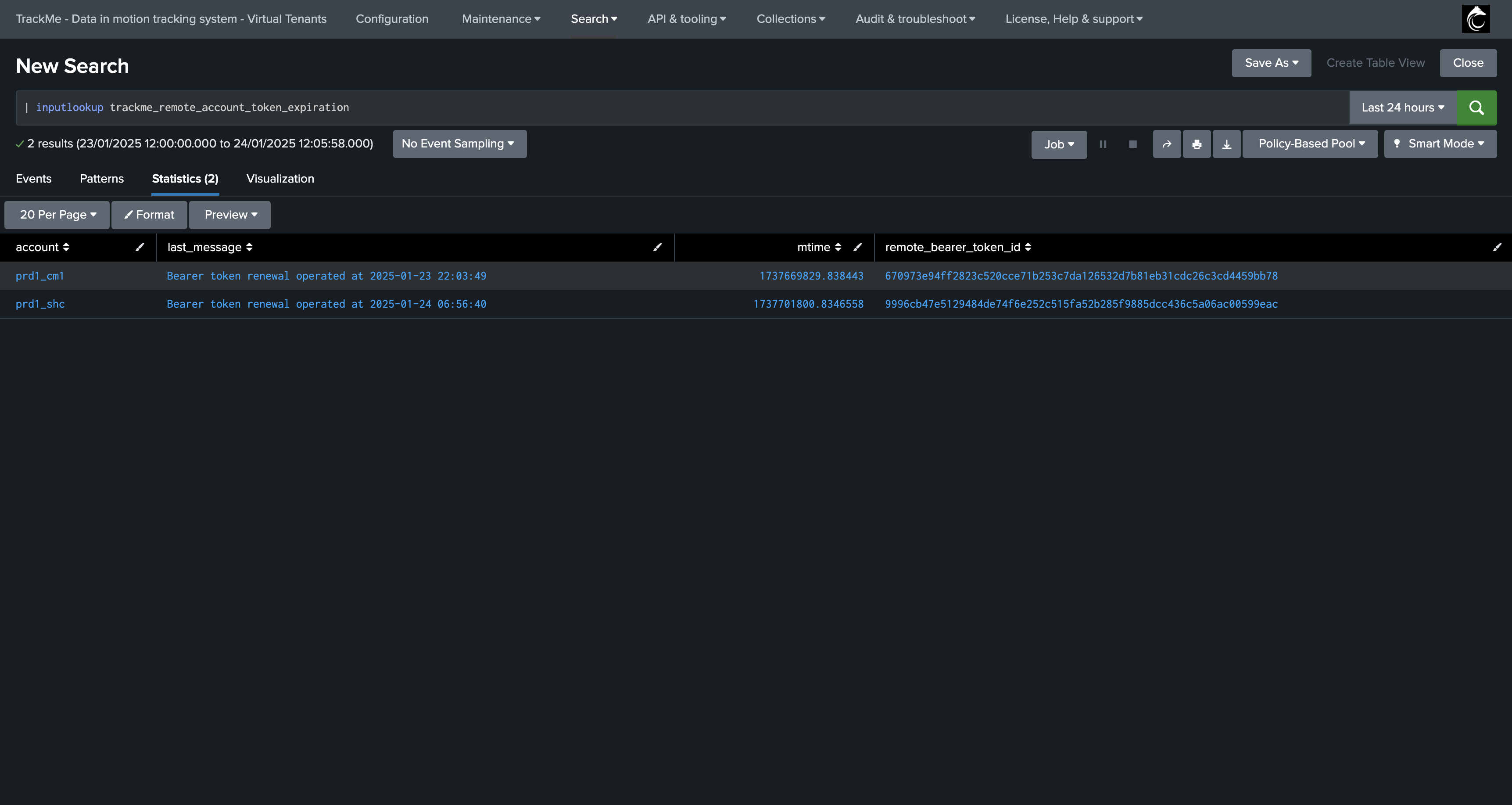
TrackMe stores the metadata related to the bearer tokens rotation in the KVstore collection trackme_remote_account_token_expiration, you can access this collection using the following SPL search:
| inputlookup trackme_remote_account_token_expiration
How to access detailed logs about the tokens rotation process?
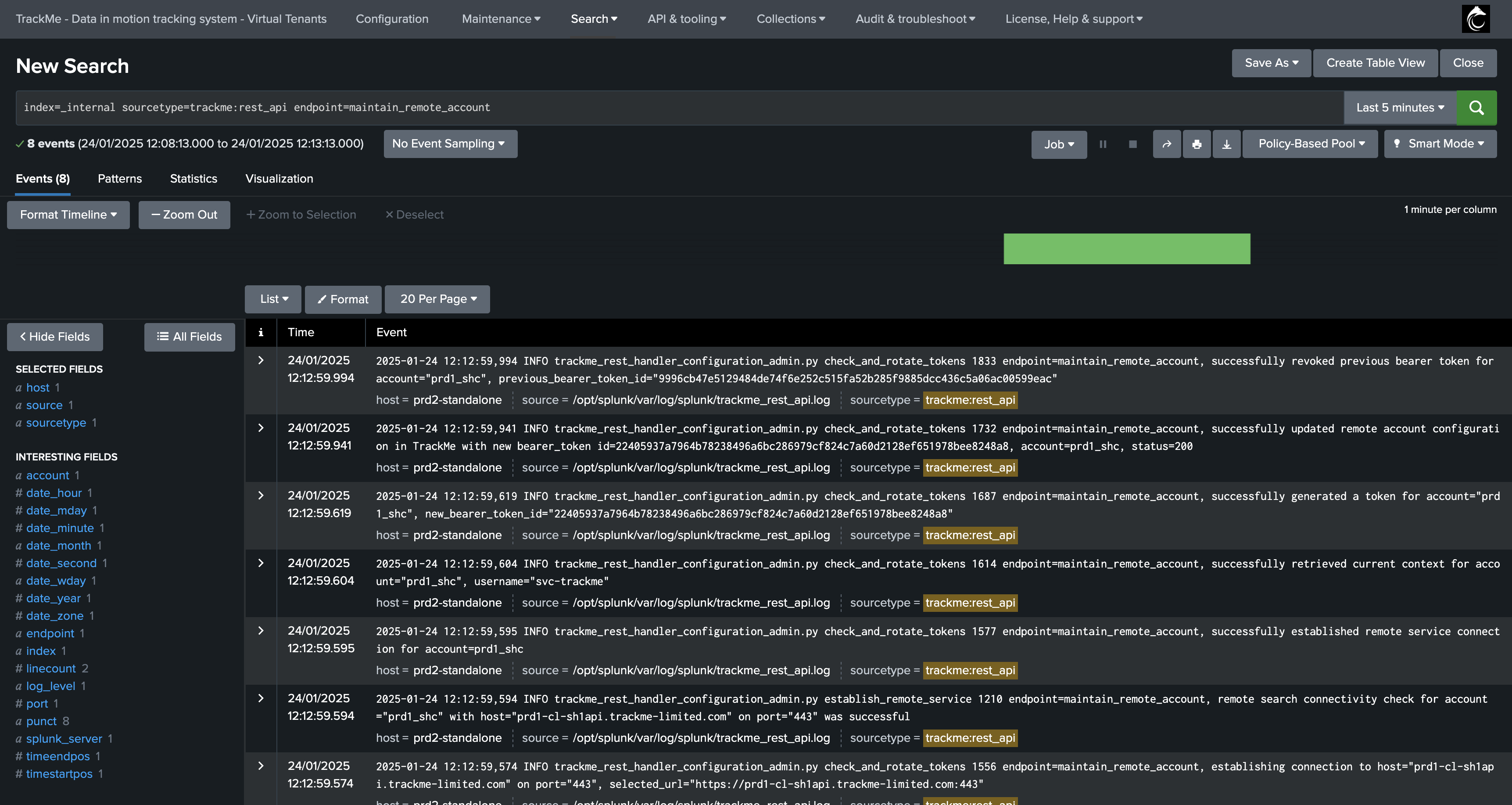
Logs are part of the TrackMe REST API logs:
index=_internal sourcetype=trackme:rest_api endpoint=maintain_remote_account
How can I force the rotation of a bearer token?
The rotation of the bearer token can be manually requested and performed by calling the TrackMe REST API endpoint, you can use the following SPL search:
| trackme mode=post url="/services/trackme/v2/configuration/admin/maintain_remote_account" body="{'accounts': '<account name>', 'force_tokens_rotation': 'true'}"
Note: replace <account_name> with the actual name of the account, or use * to rotate all accounts.
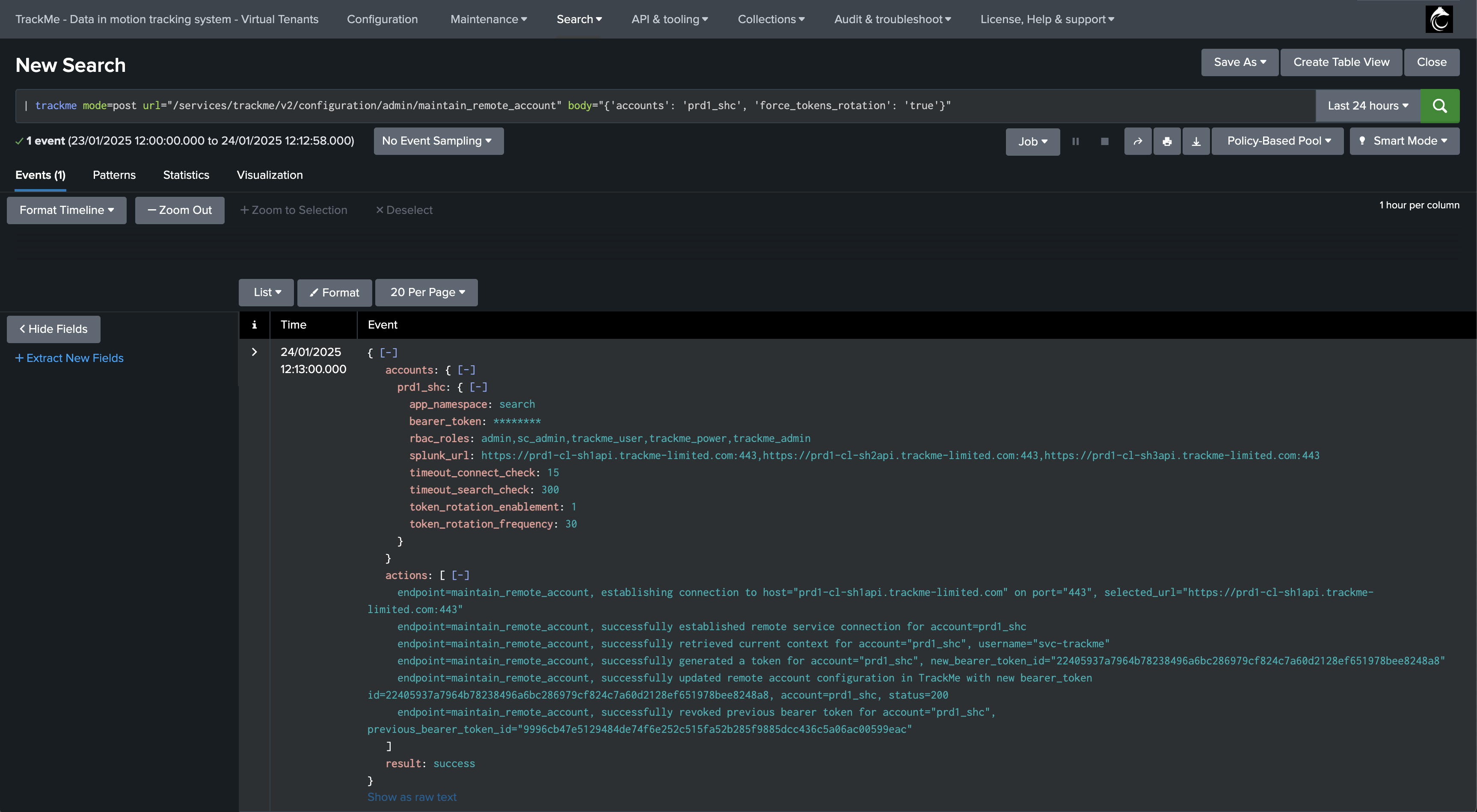
What if the token cannot be renewed?
If for some reasons, the token cannot be renewed, the process will be logged in the TrackMe REST API logs, and the token will not be revoked, the previous token will still be used:
The following search will show errors or warnings related to the tokens rotation process:
index=_internal sourcetype=trackme:rest_api endpoint=maintain_remote_account (log_level=ERROR OR log_level=WARN)
forced rotation is requested but failed:
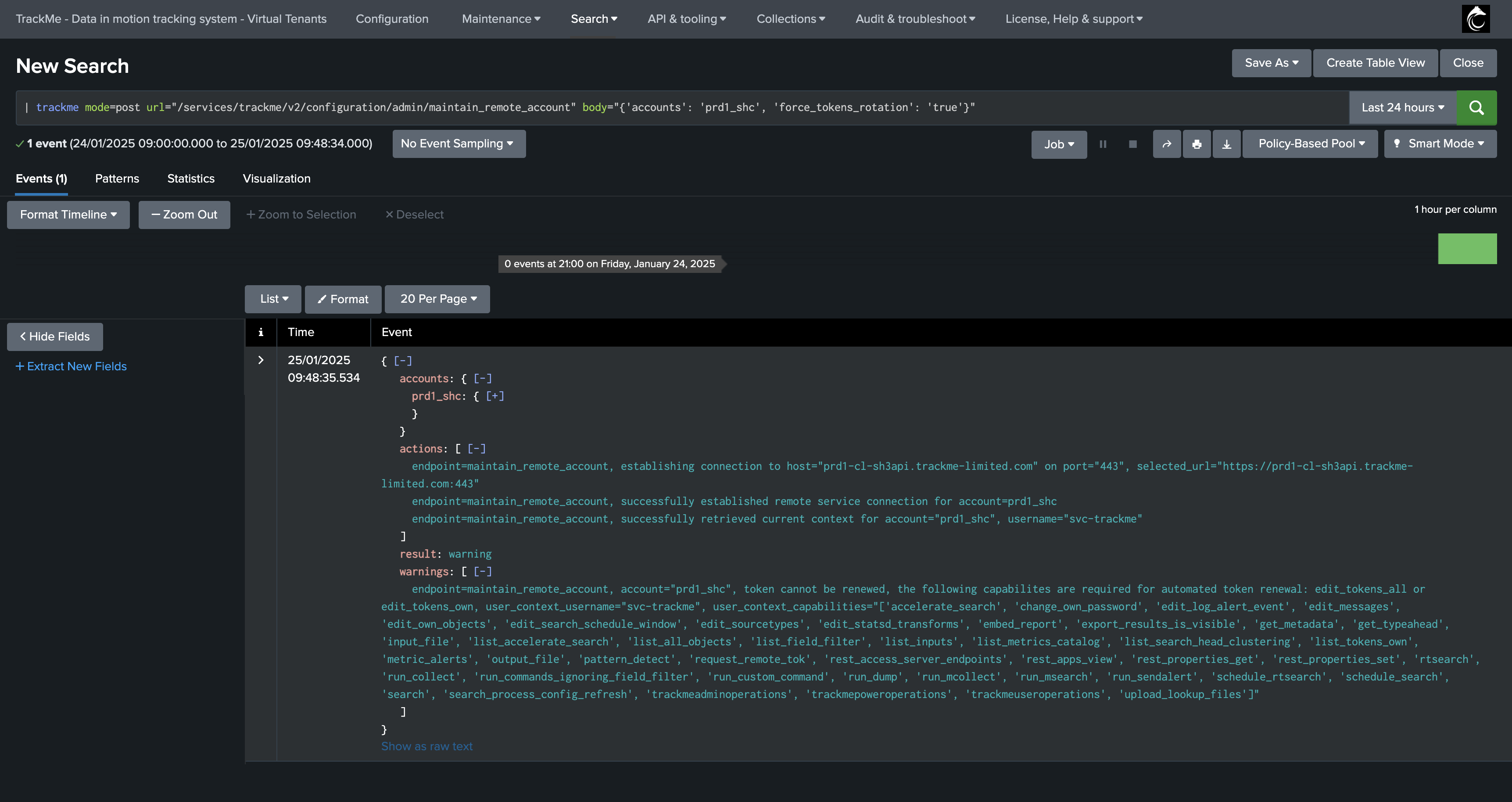
In this example, the remote user account lacks the capability to create a new token, the rotation process is aborted.

Audit Dashboard: Splunk Remote Accounts Overview
Access the Audit dashboard from the menu Audit & Troubleshooting -> Audit - Splunk Remote Accounts Overview.
Remote Accounts Commands Examples and References
Get the list of all configured remote accounts
This provides a list of all configured remote accounts, excluding the local account:
| trackme mode=get url="/services/trackme/v2/configuration/list_accounts"
| spath
| rename "accounts{}" as accounts
| table accounts
| mvexpand accounts
| where accounts!="local"
Test the Connectivity of all configured remote accounts
This command will test the connectivity of all configured remote accounts:
| trackme mode=get url="/services/trackme/v2/configuration/list_accounts" | spath
| rename "accounts{}" as accounts
| table accounts
| mvexpand accounts
| where accounts!="local"
| map maxsearches=100 search="| trackme mode=post url=/services/trackme/v2/configuration/test_remote_account body=\"{'account': '$accounts$'}\""
| trackmeprettyjson fields=_raw
| spath
Get the detailed including the bearer token for all configured remote accounts
This command will provide the detailed information about all configured remote accounts, including the bearer token:
| trackme mode=get url="/services/trackme/v2/configuration/list_accounts" | spath
| rename "accounts{}" as accounts
| table accounts
| mvexpand accounts
| where accounts!="local"
| map maxsearches=100 search="| trackme mode=post url=/services/trackme/v2/configuration/get_remote_account body=\"{'account': '$accounts$'}\""
| trackmeprettyjson fields=_raw
| spath
Force the rotation of the bearer token for all configured remote accounts
This command will force the rotation of the bearer token for all configured remote accounts in a single command:
| trackme mode=get url="/services/trackme/v2/configuration/list_accounts" | spath
| rename "accounts{}" as accounts
| table accounts | mvexpand accounts
| where accounts!="local"
| map maxsearches=100 search="| trackme mode=post url=/services/trackme/v2/configuration/admin/maintain_remote_account body=\"{'accounts': '$accounts$', 'force_tokens_rotation': 'true'}\""
| trackmeprettyjson fields=_raw
Get the token expiration metadata for all configured remote accounts and the time since the last rotation
This command will provide the token expiration metadata for all configured remote accounts and the time since the last rotation:
| inputlookup trackme_remote_account_token_expiration | eval keyid=_key
| eval _time=mtime
| eval time_since=tostring(round(now()-mtime), "duration")